TridiumのNiagara Framework®は、ビル管理、産業オートメーション、スマートインフラ環境における多様なデバイスを接続、管理、制御するために設計された最先端のソフトウェアフレームワークです。これは、HVAC、照明、エネルギー管理、セキュリティなどのさまざまなシステムをシームレスに相互運用できるようにするミドルウェアプラットフォームとして機能し、世界中のさまざまな業界のモノのインターネットIoT)技術にとって重要なバックボーンとなっています。
Recently, researchers at Nozomi Networks uncovered 13 vulnerabilities affecting the Tridium Niagara Framework. These vulnerabilities are fully exploitable if a Niagara system is misconfigured, thereby disabling encryption on a specific network device (which produces a warning on the security dashboard.) If chained together, they could allow an attacker with access to the same network — such as through a Man-in-the-Middle (MiTM) position — to compromise the Niagara system. However, this would depend on a specific network service being configured without encryption, allowing the attacker to collect sensitive data from the network.
これに対し、Tridiumは迅速にセキュリティ勧告を発表し、これらの脆弱性に対応するパッチをリリースしました。
このブログポストでは、Tridium Niagara Framework®で発見された知見、その潜在的な影響、および推奨される緩和策について説明します。
リサーチ範囲
Tridium (a Honeywell company)によって開発されたNiagara Framework®(以下「Niagara」)は、単一の環境内で多様なオペレーションシステムとデバイスを統合、管理、制御するために広く採用されているプラットフォームです。
Niagaraは、異なるメーカーのセンサー、コントローラー、機器を接続し、それぞれの通信プロトコルを統一されたデータモデルに変換する、ベンダーニュートラルなソリューションを提供します。
技術的な観点から見ると、Niagaraは2つの主要なソフトウェアコンポーネントで構成されており、1つのハードウェアデバイス上にインストールされ、両方が動作する:
- プラットフォームは、Niagaraステーションの作成、デプロイ、実行、監督に必要なコアサービスを提供する基礎となるソフトウェア環境です。
- ステーションは、デバイスと通信し、データを処理し、監視と制御のためのユーザーインターフェ イスを提供するオペレーションコンポーネントである。
これら2つのコンポーネントは、エンジニア、開発者、インテグレーターのための主要なグラフィカル・ユーザー・インターフェースとして機能する、統合開発・設定ツールであるNiagara Workbenchを通じて管理することができます。

Niagaraは重要なシステムを接続することが多く、時にはIoT 技術と情報技術(IT)ネットワークの橋渡しをすることもあるため、価値の高い標的となる可能性があります。Niagaraの脆弱性は、デジタル資産を脅かすだけでなく、商業用不動産、ヘルスケア、輸送、製造、エネルギーなどのセクター全体の安全性、生産性、サービスの継続性に影響を与え、他の現実世界の結果につながる可能性があります。
脆弱性の潜在的影響
これらの脆弱性は、Niagaraシステムが誤って設定され、特定のネットワークデバイスの暗号化が無効化された場合(セキュリティ・ダッシュボードに警告が表示される)、完全に悪用される可能性があります。これにより、以下のことが可能になります:
- 横移動 (T1210 - リモートサービスの悪用):攻撃者は侵害されたデバイスを橋頭堡として、組織のネットワークを横 断し、他のIoT ITシステムを標的にする可能性があります。
- 運用の中断 (T1499 - エンドポイントサービス拒否):悪意のある行為者は、ビルオートメーションプロセスを変更したり、重要なシステムを無効にしたり、より広範な機能停止を引き起こしたりする可能性があり、安全性のリスク、サービスの中断、金銭的損失につながる。
Niagaraを搭載したシステムによって制御される重要な機能を考えると、インスタンスがTridiumのハードニングガイドラインとベストプラクティスに従って構成されていない場合、これらの脆弱性は運用の回復力とセキュリティに高いリスクをもたらす可能性があります。
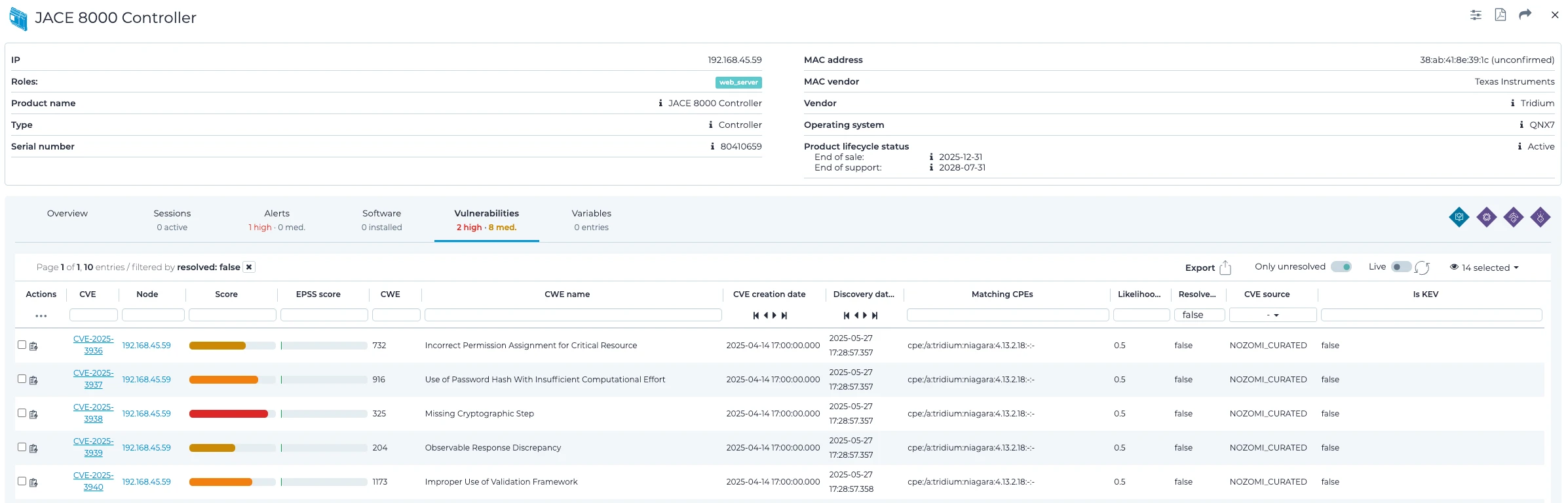
脆弱性リストと影響を受けるバージョン
Nozomi Networks 、Niagara Frameworkバージョン4.13にこれらの脆弱性を発見しました。さらに、以下のバージョンも影響を受けることが確認された:
- Niagara FrameworkおよびNiagara Enterprise Securityバージョン4.10u10以前
- Niagara FrameworkおよびNiagara Enterprise Securityバージョン4.14u1以前
以下の表は、Tridium が確認した脆弱性の一覧である。確認された13件の問題のうち5件が2つのCVEに統合され、合計10件のCVEが存在することに注意してください。結果は、CVSS 3.1スコアで最も深刻なものから最も深刻でないものへとソートされています。
脆弱性スポットライト
上記の脆弱性を注意深く分析した結果、攻撃者がネットワーク内部(隣接攻撃者)にアクセスすることから始め、 ネットワーク内のNiagaraベースのターゲットデバイスを侵害することを可能にする、説得力のある攻撃チェーンを特定 しました。これには、Station と Platform の両方を侵害し、最終的にデバイス自体でルートレベルのリモートコード実行(RCE)を達成することが含まれます。
攻撃の連鎖には2つの脆弱性が絡んでいます。
3943
Niagaraフレームワークは、状態を変更するすべてのHTTPリクエストを検証し、クロスサイトリクエストフォージェリ攻撃を防ぐためにCSRFトークンを採用しています。しかし、分析の結果、CSRFリフレッシュトークンはNiagara・ワークベンチ・ソフトウェアによって /コード エンドポイント、特に スパイ 機能を使用する。 ゲット メソッドを使用します。GET リクエストで送信されたデータは多くの場合ログに記録され、CSRF トークンはセッション全体で変更されないため、攻撃者はログから CSRF トークンを取得し、悪意のある CSRF 攻撃に悪用することができます。以下は /コード エンドポイントに CSRF リフレッシュトークンを GET メソッドで渡します。
Niagara Workbench の管理パネルと対話すると、さまざまな HTTP 要求を通じて CSP 違反レポートが頻繁にトリガされることを強調しておきます。その結果、refresh anti-CSRF トークンを含む要求がログに記録されます。さらに、Syslog が有効になっている場合、これらのログは、暗号化されていないチャネルを介してネットワーク経由で送信される可能性があり、トークンが暴露されるリスクが高まります。
以下は、特定の CSP に送信された CSP レポートの生成例である。 /CSPレポート エンドポイントである:
CSP 違反レポートはさらに、Syslog を介してネットワーク上に送信される以下のログを生成します。

その結果、Syslogサービスが暗号化されていないチャネルを使用してデータを送信するように構成されている場合、ネットワークトラフィックをスニフする能力を持つ隣接する攻撃者(例えば、MiTM攻撃を通じて)は、アンチCSRFリフレッシュトークンを傍受することができる。
3944
Niagara Framework®は、管理者が機密ファイルにアクセスしたり変更したりすることを制限するセキュアなファイル転送機能を提供します。 /etc/dhcpd/dhcpd.conf ファイルを上書きすることができます。管理者権限を持つ認証済みの攻撃者は、このファイルを上書きして特定の dhcpd.conf フック コミット時, リリース時そして 期限切れ - rootで任意のコードを実行する Niagara QNX ベースのオペレーティング・システム上の特権。
以下はオンコミットフックの例である。 dhcpd.conf ファイルのようなルートで読み取り可能なファイルの内容の流出を引き起こす可能性がある。 /etc/passwd そして /etc/shadow の中にデータを保存する。 /tmp/out ファイル。
攻撃の前提条件
この攻撃連鎖を成功させるには、2つの条件を満たす必要がある:
- 攻撃者は、Tridium Niagara デバイスを発着するトラフィックを覗き見するか、MITM(Man-in-the-Middle)攻撃を実行できなければなりません。
- Syslog機能を有効にし、ログを暗号化せずにSyslogサーバーに転送するように設定する必要があります(この設定は、セキュリティダッシュボードに警告を表示します)。
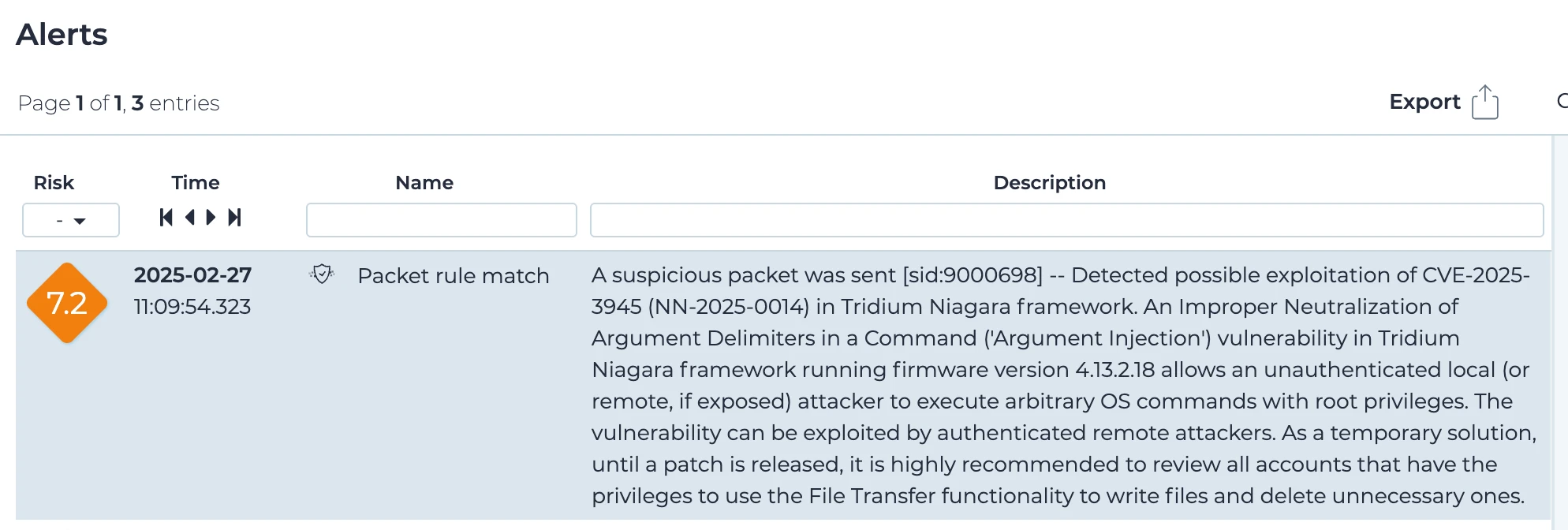
図 3 は、Niagaraベースの Tridium Jace 8000 がローカル・ネットワーク上に配置されている場合に考えら れる攻撃シナリオを示しています。

これらの前提条件が満たされれば、攻撃者は以下のステップを実行できる:
1.ネットワーク経由で送信されるアンチ CSRF リフレッシュトークンを傍受する(CVE-2025-3943):前述の通り、CVE-2025-3943を 悪用することで、ネットワークをスニッフィングしている隣接攻撃者は、Niagara・ワークベンチ・ソフトウェアによって生成されたCSP違反レポートによってネットワーク経由で送信されるアンチCSRFトークンを傍受するために、Syslogネットワークトラフィックを分析することができます(図4)。

2.ログ収集のエスカレーション:アンチCSRFリフレッシュトークンを取得した後、攻撃者はCSRF攻撃を偽造し、管理者を騙して以下のような細工されたリンクにアクセスさせます。 /ord?spy:/logSetup/ALL- web.jetty$3ftoken$...のログレベルを変更する。 ウェブジェッティ コンポーネント すべて.この設定により、すべての受信HTTPリクエストとレスポンスの内容が完全にログに記録されます(図5 - ステップ1と2)。
3.セッション・ハイジャック:ネットワーク経由で送信された Syslog データを分析することで、攻撃者は管理者の JSESSIONID セッショントークンを抽出します。このセッション ID を使って、攻撃者は完全な管理者権限でステーションに接続し、永続的なアクセスのために新しいバックドア管理者ユーザーを作成します(図 5 - ステップ 3 と 4)。

4.証明書の盗難によるプラットフォームの侵害:管理者アクセスを利用し、攻撃者はデバイスの TLS 証明書に関連付けられた秘密鍵をダウンロードするため の専用機能を悪用する。ステーションとプラットフォームの両方が同じ証明書と鍵インフラを共有しているため、攻撃者はデバイスに対す る今後の全てのセッションを、たとえそれが TLS で暗号化されていたとしても、MitM することができます。これでプラットフォームへのフルアクセスが可能になりました(図 6)。

5.ルート・リモート・コード実行(RCE):攻撃者はプラットフォームを制御することで、デバイス上でルートレベルの RCE を提供する脆弱性 CVE-2025-3944 を直ちに悪用し、完全な乗っ取りを達成します。
最終的な RCE ステップが追求されなくても、このテクニックは、Windows システム上で実行されるインストールを含む、Station と Platform 環境の両方を完全に危険にさらすことができます。
緩和策と提言
Tridiumは、Niagara Frameworkのセキュリティパッチによってこれらの脆弱性に対処しました。Tridium製品のセキュリティチームにより、セキュリティレポートが発表されました。資産所有者および運営 者は、以下のことを強く推奨します:
- 詳細なガイダンスについては、Tridium のセキュリティアドバイザリを参照してください。
- 影響を受けるNiagaraのインストールを、できるだけ早く最新のパッチ付きバージョンに更新してください。
- ネットワークのセグメンテーションを実施し、システムの露出を制限する。
- 例えば、Nozomi Networks Guardian の脆弱性と脅威の検出機能を使用して、Niagaraデバイスに関連する脆弱な資産や不審なアクティビティが存在しないか、ネットワークトラフィックを監視 します。詳しくは、デモをご請求ください。
重要なインフラを保護し、業務の完全性を維持するためには、迅速な対応が不可欠である。