直近のイラン紛争を踏まえ、Nozomi Networks Labsは5月から6月にかけて、イランの有名な脅威行為者グループからのサイバー攻撃が133%増加していることを確認した。これまでNozomi Networks Labsのリサーチャーが観測したところでは、CISAが6月30日に発表したファクトシートや、先週の米国土安全保障省による国家テロ諮問システム速報で警告されているように、米国企業が主な標的となっているようだ。
当社のリサーチャーは、MuddyWater、APT33、OilRig、CyberAv3ngers、FoxKitten およびHomeland Justiceが運輸および製造組織を標的としていることを確認しました。米国内外の産業および重要インフラ組織は、警戒を怠らず、セキュリティ態勢を見直すよう求められています。Nozomi Networks お客様は、Nozomi Threat Intelligence ご覧いただき、これらのグループによる活動の兆候をご確認ください。Nozomi Networks Threat Intelligence フィード(別途Mandiant TI Expansion Packを含む)を購読している場合、シグネチャは以前から導入されているため、カバーされています。
サイバー脅威の最新動向
日々の業務の一環として、Nozomi Networks Labsのリサーチャーは、国家グループを含む様々な脅威行為者を常に追跡しています。私たちは、参加しているお客様から匿名化されたテレメトリーを受信し、これらのアクターに関連する攻撃に関する現在の傾向を公に共有することができます。
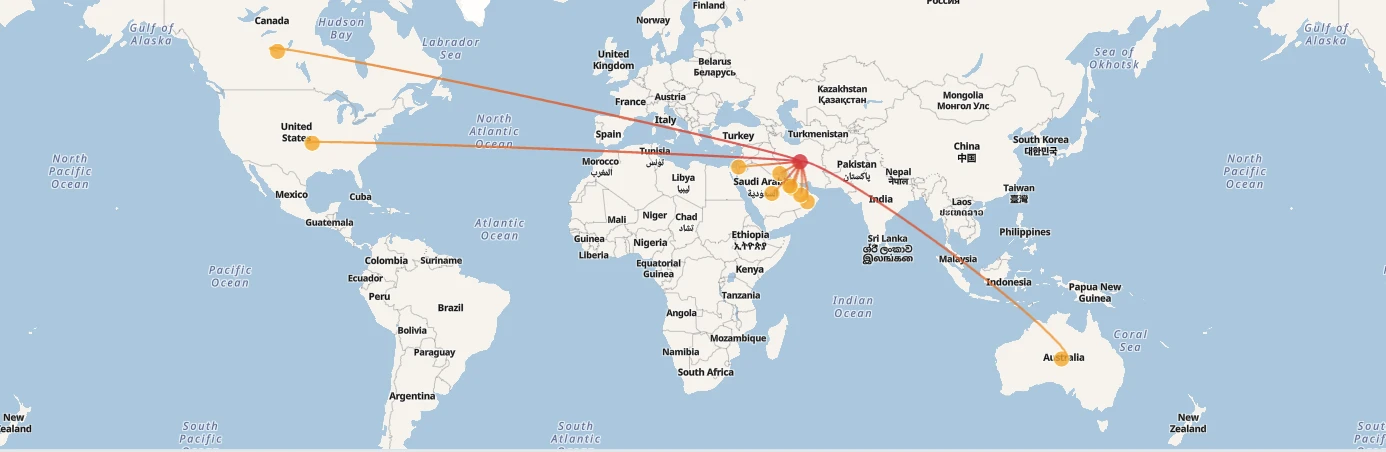
5月から6月にかけて、イランの脅威関係者による攻撃が28件観測された。その前の2カ月間が12件であったのと比べると、133%の増加である。
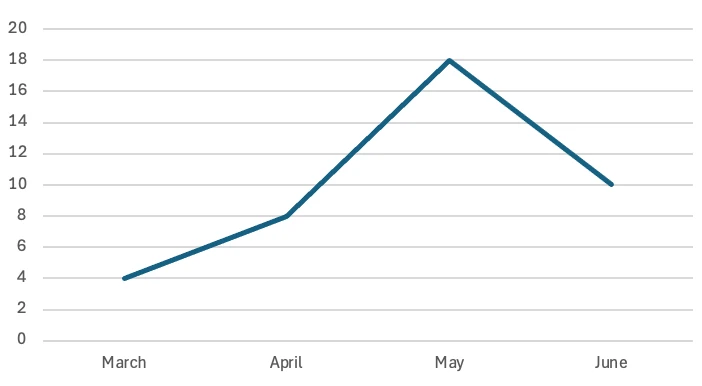
当然のことながら、攻撃は米国内の組織を標的としていた。最も活発なイランの脅威行為者はMuddyWaterで、以下で詳しく取り上げる。この2カ月間で、主に運輸と製造に関連する少なくとも5社の米国企業を攻撃した。続いて、APT33が少なくとも3社の米国企業を攻撃しています。最後に、OilRig、CyberAv3ngers、Fox Kitten、Homeland Justiceが、それぞれ少なくとも2つの異なる米国企業に対する攻撃に関連していることが確認できました。
興味深い事実として、今回CyberAv3ngersは、昨年12月に発見された悪名高いOTOrpaCrab別名IOCONTROLマルウェアを利用した前回の攻撃に関連するIPアドレスを再利用することにしました。OT、IoT 、ITのいずれの領域が狙われているかにかかわらず、Nozomi Networks Labsは、これらすべての攻撃者を注意深く監視し、顧客が保護されていることを確認していきます。
グローバルな脅威アクターの活動
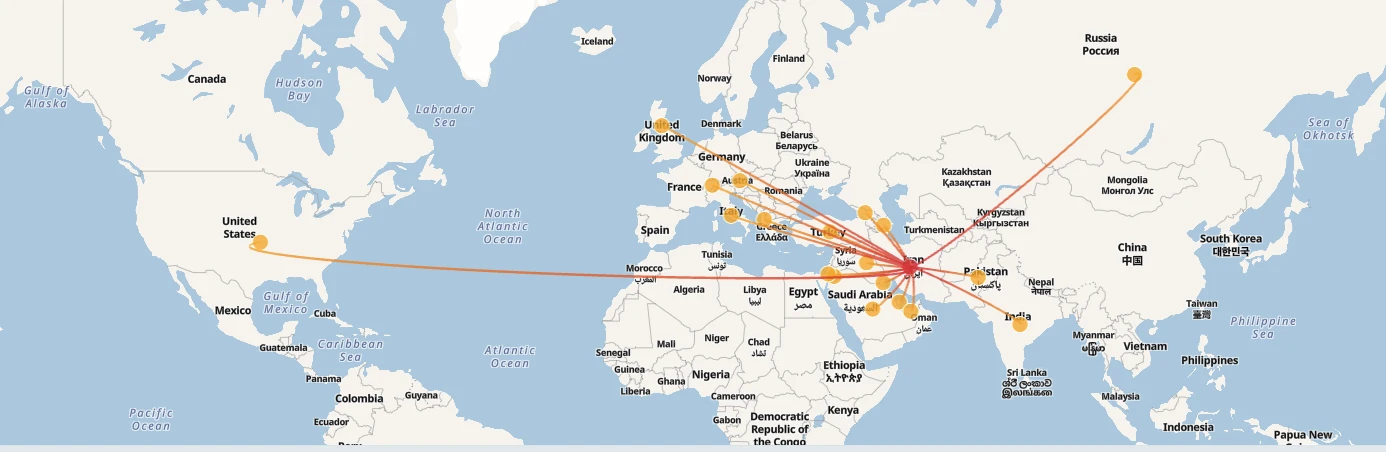
以下は、当社のThreat Intelligence サービスで報告されているイランの脅威行為者の活動を国別にハイライトしたNozomi Platformの画像です。
マディーウォーター
MuddyWater(SeedWormとしても知られる)は、イランを発生源とする脅威行為者グループである。2017年から活動を開始し、主に中東諸国、特にサウジアラビア、イラク、トルコを標的としています。彼らの主な標的は、政府機関、電気通信、エネルギー部門です。
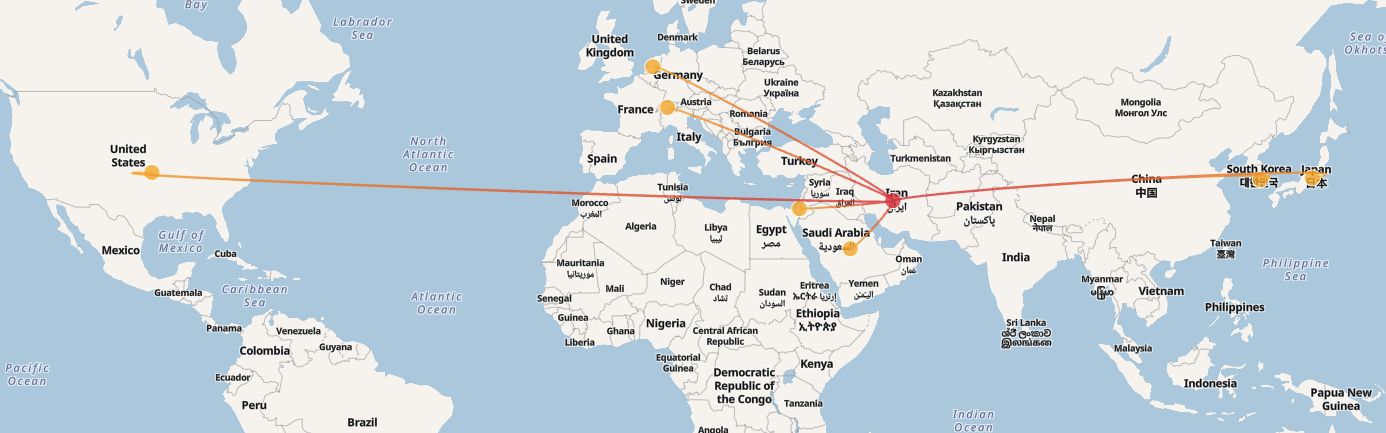
APT33
APT33(別名Elfin)は、イランから発生したと考えられている脅威行為者グループです。彼らは、航空宇宙、エネルギー、石油化学分野の組織を標的としたサイバースパイ活動に関与しています。APT33は2013年に初めて観測され、現在に至るまで活動を続けており、イランの国益を増進させるために機密情報を盗むことに重点を置いています。
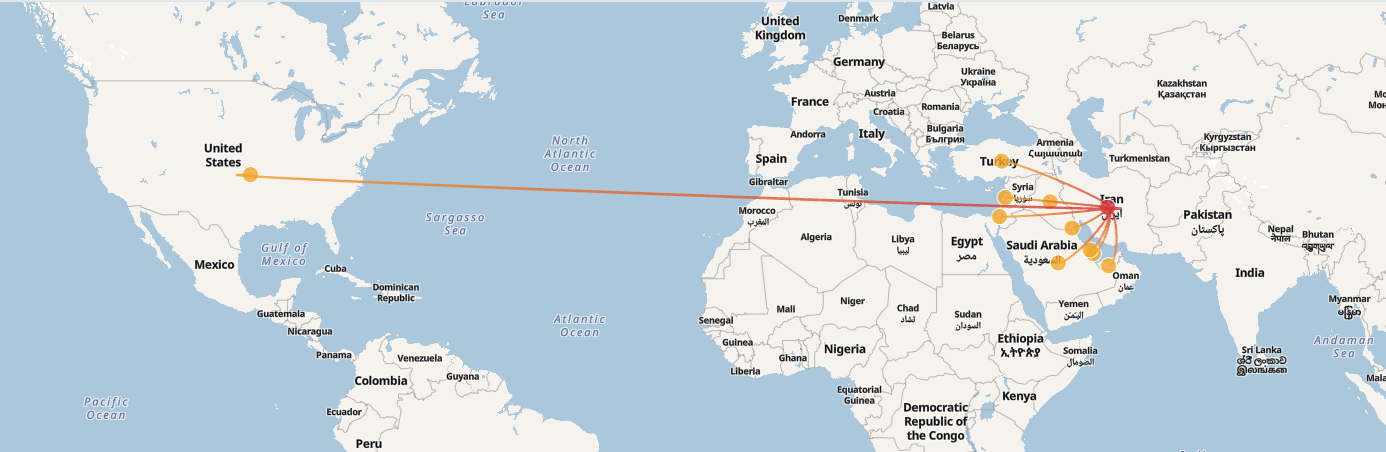
オイルリグ
OilRig(APT34、Helix Kittenとしても知られる)は、イランを発生源とする脅威行為者です。彼らは少なくとも2014年から活動しており、主にサウジアラビア、アラブ首長国連邦、カタールなどの中東諸国を標的としています。彼らの焦点はスパイ活動であり、政府、金融、エネルギー、通信部門からの機密情報を収集することです。このグループは、標的のネットワークに侵入するためにスピアフィッシングメールやカスタムマルウェアツールを使用することで知られています。
サイバーエージェント
CyberAv3ngersは、重要インフラ、政府機関、民間組織を標的としたサイバースパイ活動や政治的動機に基づく作戦で知られるイランの脅威行為者グループです。このグループの特徴は、高度な持続的脅威(APT)戦術の洗練された使用、カスタムメイドのマルウェア、スピアフィッシングキャンペーン、ゼロデイ脆弱性を活用して目的を達成することです。CyberAv3ngersは通常、中東や欧米諸国を中心に活動し、その活動をイランの地政学的目標と一致させています。
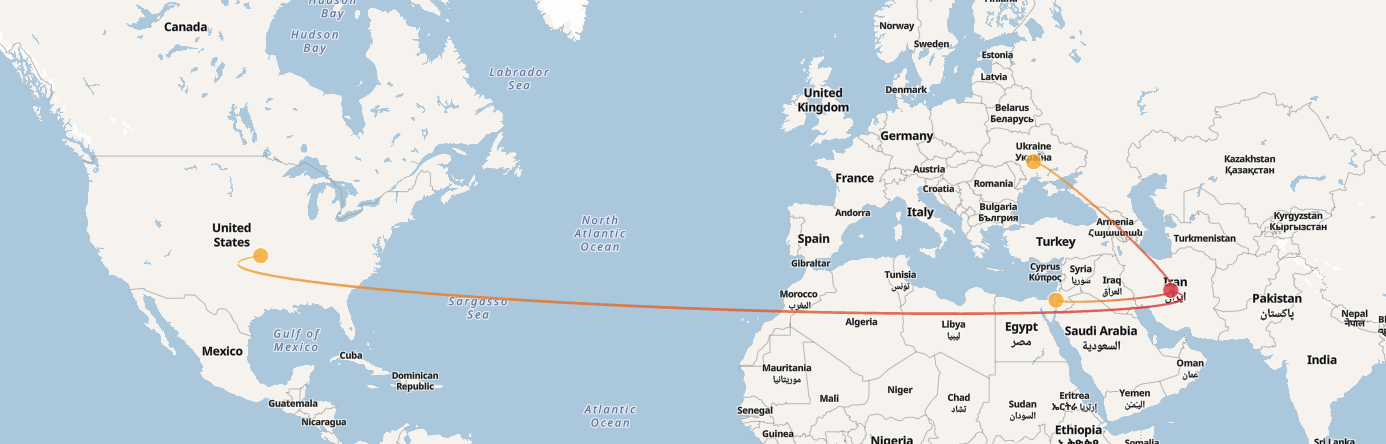
フォックス・キトン
Fox Kitten(別名Pioneer Kitten)は、高度に洗練されたイランの高度持続的脅威(APT)グループで、少なくとも2017年から活動しています。このグループは国家が支援し、イランの広範なサイバースパイおよび破壊工作組織の一部として活動していると広く考えられています。Fox Kittenは主に、サイバースパイ活動、長期的なアクセス、潜在的な破壊的または破壊的なサイバー作戦の事前準備に重点を置いています。特に中東をはじめとするイランの地政学的利益にとって戦略的に価値のある組織を標的としています。
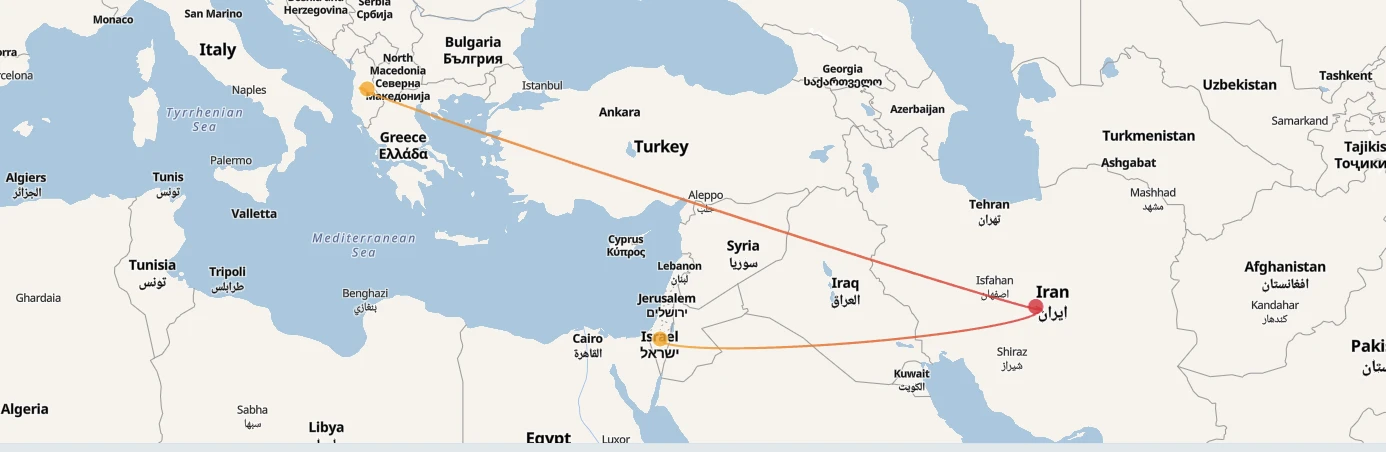
ホームランド・ジャスティス
Homeland Justiceは、イランの国家支援によるサイバー脅威集団である。2022年にアルバニア政府のインフラを標的とした一連の破壊的サイバー攻撃で有名になった。
Nozomi 助けに来た
現代世界では、世界的な紛争や地域的な紛争は常にサイバー脅威要因の活発化を伴っており、時にはその結果において重要な役割を果たすこともある。一年中、基本的なデューディリジェンスを行うことに加え、日々、これらの脅威を追跡することは、常に最新の状況を把握し、組織が可能な限り最高のサイバーセキュリティ態勢を構築するために不可欠です。Nozomi Networks、このような脅威に真剣に取り組んでいます。私たちは、実用的なインテリジェンスを継続的に更新される検知ロジックに変換し、TI Expansion Pack Powered by Mandiantを含む専用のThreat Intelligence サブスクリプションや、私たちのセンサーがなくても、あらゆるサイバーセキュリティソリューションとシームレスに統合できるスタンドアロンのThreat Intelligence Feedを通じて、お客様に毎日お届けしています。
重要なインフラを守る使命を果たすため、私たちは世界中の組織に対し、サイバー攻撃との戦いに参加するよう呼びかけています。
IoCリスト
- 159.100.6[.]69
- 169.150.227[.]230
- 95.181.161[.]50
- 164.132.237[.]65
- 5.199.133[.]149
- 104.200.128[.]71
- 104.200.128[.]206
- 31.192.105[.]28
- 185.118.66[.]114
- 194.187.249[.]102
- 185.162.235[.]29
- 144.202.84[.]43
- 64.176.173[.]77
- 64.176.172[.]101
- 64.176.172[.]235









