Nozomi Networks Enters Next Phase of Growth as Mitsubishi Electric Completes Acquisition
Read the Newsどのようなテクノロジー環境においても、基本的なサイバーセキュリティの衛生管理を実践することは、レジリエンス(回復力)に大きく貢献します。多くの基本的なサイバーセキュリティの実践は IT からOT へと引き継がれ、パッチの適用頻度の低さを補うために、セグメンテーションや継続的なモニタリングなどの分野に重点が置かれています。ベストプラクティスには以下が含まれます:
産業用ネットワークに特化したNozomi Networks プラットフォームは、自動化されたアセットインベントリーと継続的なモニタリングによる可視性を提供することに優れています。
ネットワークで何が起きているかを可視化することは、サイバーセキュリティの要です。目に見えないものを管理することはできません。インターネットには?どのプロトコルを使って、何が何に接続しているのか?誰が、何に、どこからログインしているのか?不正なトラフィックはないか?コントロールやポリシーは設計通りに機能しているか?これらの質問には、可視化なしでは答えられません。
産業環境では、ネットワークの可視性はサイバーセキュリティだけでなく、運用上の異常やその他の問題のトラブルシューティングにも不可欠です。例えば、データ・トラフィックの異常を検出することは、サイバー侵入の可能性を示すだけでなく、早急な対処が必要な機器の故障を示す可能性もあります。
Nozomi Networks プラットフォームは、ネットワークモニタリング、エンドポイントモニタリング、ワイヤレスモニタリング、smart polling、様々なデータ収集方法を用いて、すべての資産とそのリスクレベルを、それらがアクティブに通信していないときでも継続的に可視化します。
インストールが完了するとすぐに、プラットフォームはICSネットワークトラフィックの分析を開始し、ネットワーク全体のマクロ・ビューだけでなく、個々のアセットやノードを表示するインタラクティブな視覚化を構築します:
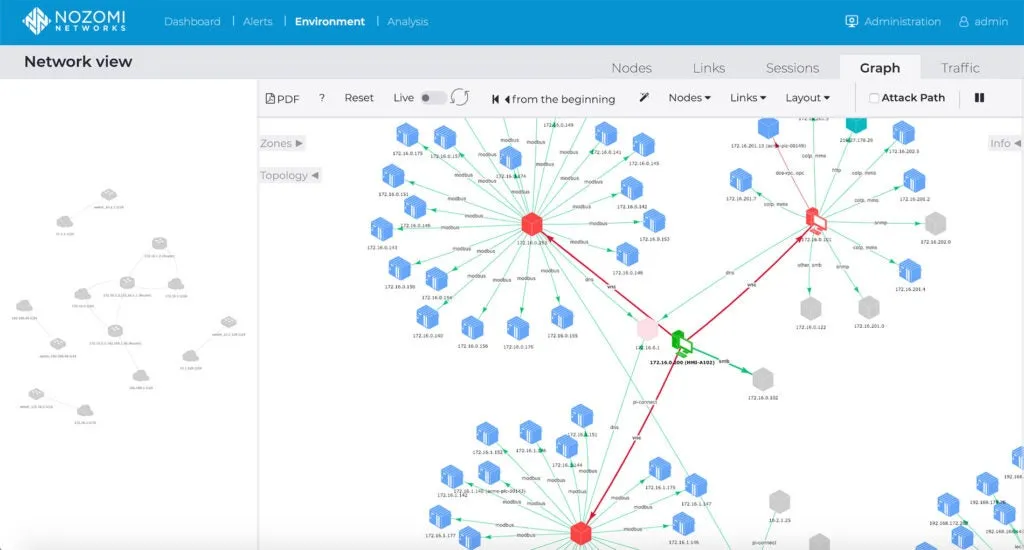
このグラフはまた、ネットワーク通信の可視性を提供し、セグメンテーションポリシー違反をハイライトする。例えば、Nozomi Networks プラットフォームは、重要な資産がインターネットと通信している時や、ファイアウォールルールやアクセス制御ポリシーの設定ミスを検出することができます。
自動化された資産管理は、ネットワークに接続されているもの、それらの主要な属性、そして理想的には運用上のトラブルシューティングや脅威の調査のための追加コンテキストについて、基礎となる可視性を提供します。自動化された資産目録は、OT 資産、接続、通信、プロトコルなどをリアルタイムで可視化することで、死角をなくします。
Networks プラットフォームは、センサーから得られたOT およびIoT デバイスのプロファイルに、AIを活用した詳細な資産情報を付加します。 Asset Intelligenceフィードを追加することで、常に最新のほぼ100%正確な資産インベントリを提供します。
ネットワークと接続された資産をリアルタイムで継続的に監視することは、OTセキュリティの要です。特殊なハードウェア、一般的でない、または独自のプロトコルを持ち、セキュリティ機能が組み込まれていないOT およびIoT デバイスの膨大な量により、従来のITシステムよりも監視と管理がはるかに難しくなっています。
継続的なモニタリングは、資産のインベントリ、パッシブなディープ・パケット・インスペクション、安全でアクティブなデータ収集、脆弱性のマッピングと優先順位付け、異常と脅威の検出など、主要なサイバー機能を網羅しています。これにより、潜在的なインシデントが業務に影響を及ぼす前に、それをキャッチすることができます。攻撃や事故が発生した場合、継続的なモニタリングから得られる情報は、その影響の大きさと対応方法をより的確に把握するのに役立ちます。
どのようなテクノロジー環境においても、基本的なサイバーセキュリティの衛生管理を実践することは、レジリエンス(回復力)に大きく貢献します。多くの基本的なサイバーセキュリティの実践は IT からOT へと引き継がれ、パッチの適用頻度の低さを補うために、セグメンテーションや継続的なモニタリングなどの分野に重点が置かれています。ベストプラクティスには以下が含まれます:
産業用ネットワークに特化したNozomi Networks プラットフォームは、自動化されたアセットインベントリーと継続的なモニタリングによる可視性を提供することに優れています。
ネットワークで何が起きているかを可視化することは、サイバーセキュリティの要です。目に見えないものを管理することはできません。インターネットには?どのプロトコルを使って、何が何に接続しているのか?誰が、何に、どこからログインしているのか?不正なトラフィックはないか?コントロールやポリシーは設計通りに機能しているか?これらの質問には、可視化なしでは答えられません。
産業環境では、ネットワークの可視性はサイバーセキュリティだけでなく、運用上の異常やその他の問題のトラブルシューティングにも不可欠です。例えば、データ・トラフィックの異常を検出することは、サイバー侵入の可能性を示すだけでなく、早急な対処が必要な機器の故障を示す可能性もあります。
Nozomi Networks プラットフォームは、ネットワークモニタリング、エンドポイントモニタリング、ワイヤレスモニタリング、smart polling、様々なデータ収集方法を用いて、すべての資産とそのリスクレベルを、それらがアクティブに通信していないときでも継続的に可視化します。
インストールが完了するとすぐに、プラットフォームはICSネットワークトラフィックの分析を開始し、ネットワーク全体のマクロ・ビューだけでなく、個々のアセットやノードを表示するインタラクティブな視覚化を構築します:

このグラフはまた、ネットワーク通信の可視性を提供し、セグメンテーションポリシー違反をハイライトする。例えば、Nozomi Networks プラットフォームは、重要な資産がインターネットと通信している時や、ファイアウォールルールやアクセス制御ポリシーの設定ミスを検出することができます。
自動化された資産管理は、ネットワークに接続されているもの、それらの主要な属性、そして理想的には運用上のトラブルシューティングや脅威の調査のための追加コンテキストについて、基礎となる可視性を提供します。自動化された資産目録は、OT 資産、接続、通信、プロトコルなどをリアルタイムで可視化することで、死角をなくします。
Networks プラットフォームは、センサーから得られたOT およびIoT デバイスのプロファイルに、AIを活用した詳細な資産情報を付加します。 Asset Intelligenceフィードを追加することで、常に最新のほぼ100%正確な資産インベントリを提供します。
ネットワークと接続された資産をリアルタイムで継続的に監視することは、OTセキュリティの要です。特殊なハードウェア、一般的でない、または独自のプロトコルを持ち、セキュリティ機能が組み込まれていないOT およびIoT デバイスの膨大な量により、従来のITシステムよりも監視と管理がはるかに難しくなっています。
継続的なモニタリングは、資産のインベントリ、パッシブなディープ・パケット・インスペクション、安全でアクティブなデータ収集、脆弱性のマッピングと優先順位付け、異常と脅威の検出など、主要なサイバー機能を網羅しています。これにより、潜在的なインシデントが業務に影響を及ぼす前に、それをキャッチすることができます。攻撃や事故が発生した場合、継続的なモニタリングから得られる情報は、その影響の大きさと対応方法をより的確に把握するのに役立ちます。