A common challenge for many electric utilities and power generators developing their NERC CIP-15-1 Internal Network Security Monitoring (INSM) program is classifying the INSM system itself. Under CIP-015-1, an INSM system isn’t pre-classified as a single asset type, such as a Protected Cyber Asset (PCA), an Electronic Access Control or Monitoring System (EACMS) or as BES Cyber System Information (BCSI). Instead, the responsible entity must evaluate the INSM system against its NERC CIP program (CIP-002 and CIP-011 processes) to determine the appropriate classification based on location, function and the data it processes.
Classifying the INSM system can significantly affect the effort required to remain compliant. A well-designed INSM program should include a clear explanation of how and why an entity categorized the system. This article offers background, justification and recommendations, but ultimately, each entity must determine its own classification.
What’s in an Acronym? Defining BCSI, EACMS and PCA
NERC has defined each of these classifications in the official NERC CIP Glossary of Terms.
- BES Cyber System Information (BCSI): Information about the BES Cyber System (BCS) that could be used to gain unauthorized access or pose a security threat to the BCS. BES Cyber System Information (BCSI) does not include individual pieces of information that by themselves do not pose a threat or could not be used to allow unauthorized access to BCS, such as, but not limited to, device names, individual IP addresses without context, Electronic Security Perimeter names, or policy statements.
- Electronic Access Control or Monitoring Systems (EACMS): Cyber Assets that perform electronic access control or electronic access monitoring of the Electronic Security Perimeter(s) or BES Cyber Systems. This includes Intermediate Systems.
- Protected Cyber Assets (PCA): One or more Cyber Assets connected using a routable protocol within or on an Electronic Security Perimeter that is not part of the highest impact BES Cyber System within the same Electronic Security Perimeter. The impact rating of Protected Cyber Assets is equal to the highest rated BES Cyber System in the same ESP.
Location, Location, Location: Inside or Outside the ESP?
The location of the INSM system and its components is the first consideration for asset classification. If the INSM system is located within the ESP, it would be either an EACMS or a PCA.

If the INSM system is located outside the ESP, it would either be an EACMS or a BCSI storage location.
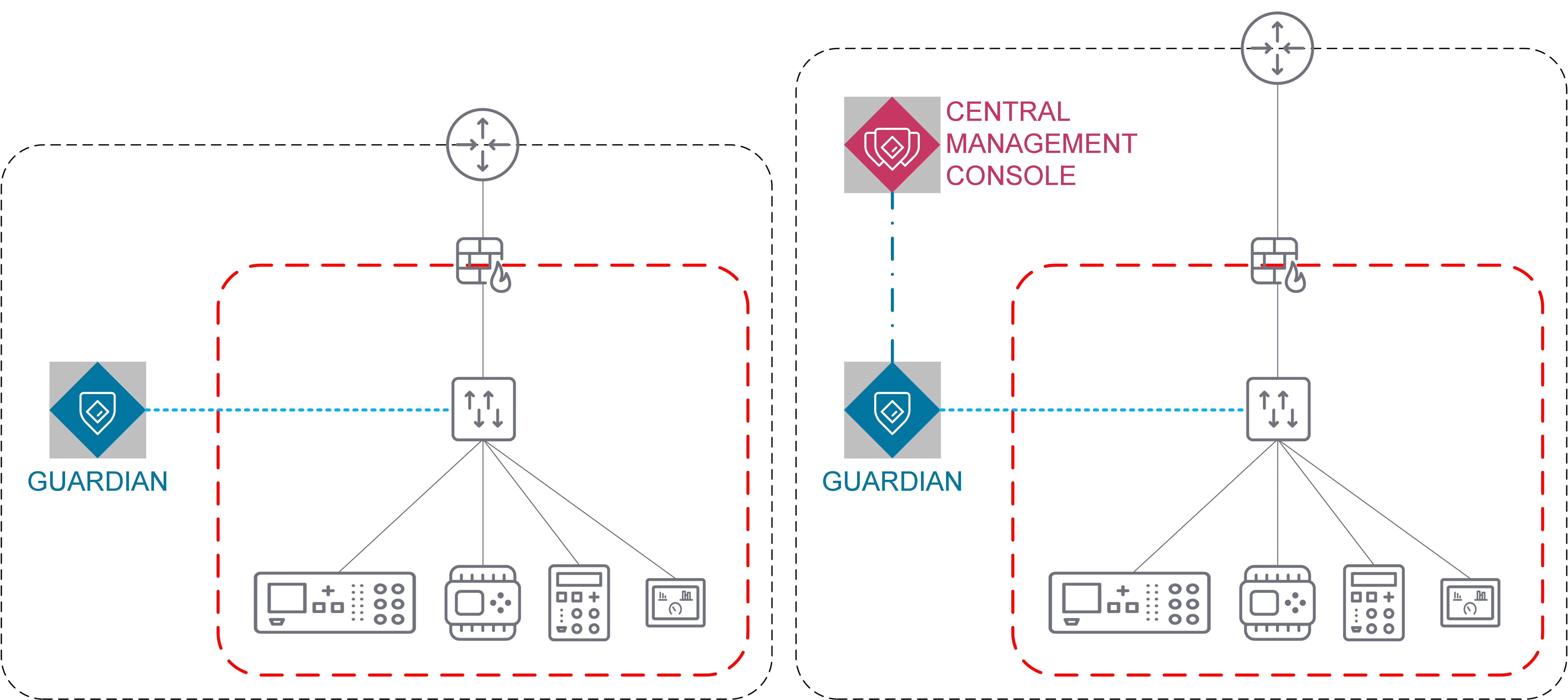
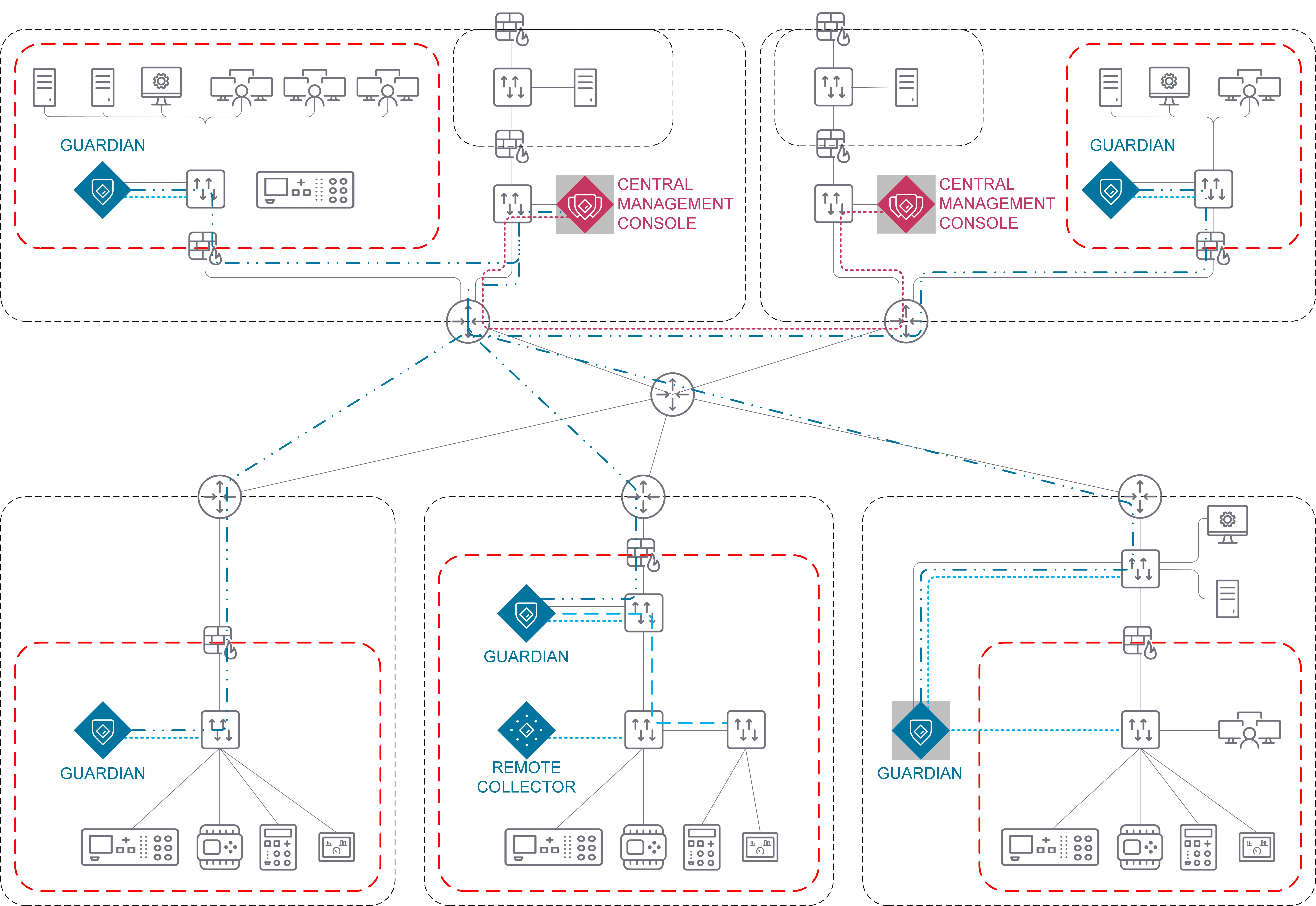
Different components of the INSM system may be located inside or outside the ESP, which may drive different classifications for each component.
When to Consider the BCSI Classification
Classifying INSM systems as BCSI storage locations results in the fewest applicable NERC CIP requirements as compared to EACMS and PCA, and therefore the least compliance overhead on an organization. This is only an option for INSM systems outside the ESP.
BCSI is typically a data classification, not a device classification. The INSM system itself would not be BCSI; rather, the information it collects and stores is usually BCSI. NERC does reference a BCSI storage location, which is a valid classification for an INSM system. This reference is in CIP-011-3 R1 Part 1.1 “Storage locations identified for housing BCSI in the entity’s information protection program.”
An INSM system does not function as an EACMS
If the INSM system does not provide electronic access control or electronic access monitoring functions for the entity, then it should not be classified as an EACMS. In most cases, an INSM cannot meet CIP-005, CIP-007 or CIP-10 requirements, even if it collects some data flows that contain information pertaining to those requirements.
For example, INSM systems may detect some successful and unsuccessful login attempts as required by CIP-007-6 R4 Part 4.1. However, an INSM system that is not defined as a system that functions in a way to meet those requirements would not be considered an EACMS.
EACMS requirements are often defined at an asset or system level, not at the network level where INSM functions. For example, CIP-007-6 R4 Part 4.1 stipulates: “Log events at the BES Cyber System level (per BES Cyber System capability) or at the Cyber Asset level (per Cyber Asset capability).”
An INSM system functions as a BCSI storage location
INSM systems collect and store detailed network traffic flow data, including IP addresses, device identifiers and communication patterns from within ESPs. Additionally, INSM systems typically provide insight into BCS topology or operational behavior. These functions align with the BCSI definition.
INSM CIP-015-1 R3 requirements align closely with data protection requirements as outlined in CIP-011-3 R1 Part 1.2: “Method(s) to protect and securely handle BCSI to mitigate risks of compromising confidentiality.”
NERC, ERO and Industry support for BCSI classification
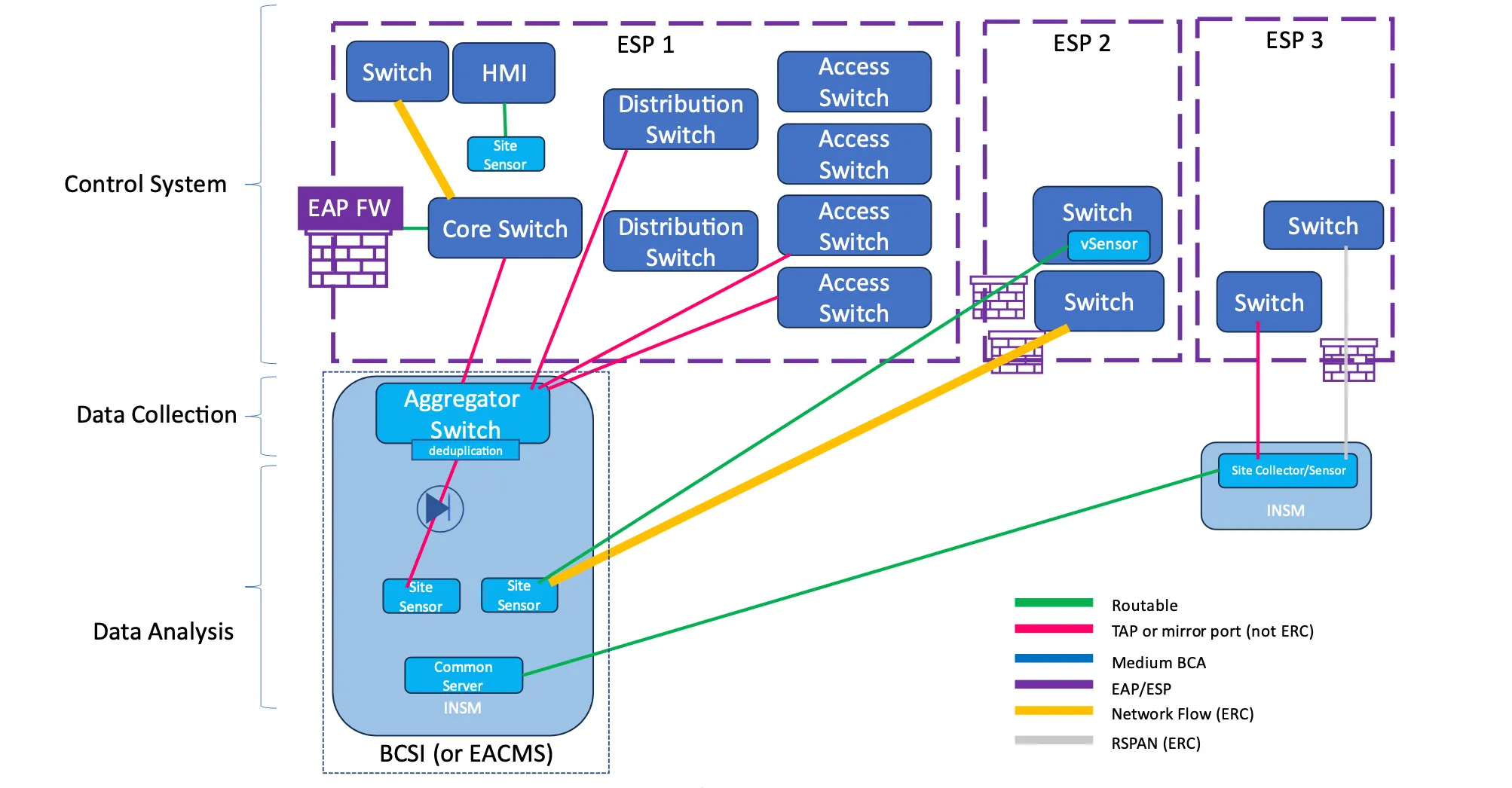
The CIP-015-01 drafting team provided support for the BCSI classification in the Technical Rationale as part of the Project 2023-03 INSM deliverables, including language and a reference architecture that references the BCSI classification:
The Responsible Entity’s existing process(es) should be referenced to determine if the INSM system and its components are PCA, EACMS, or exempted from applying protections other than those required for BES Cyber System Information (BCSI) protection.
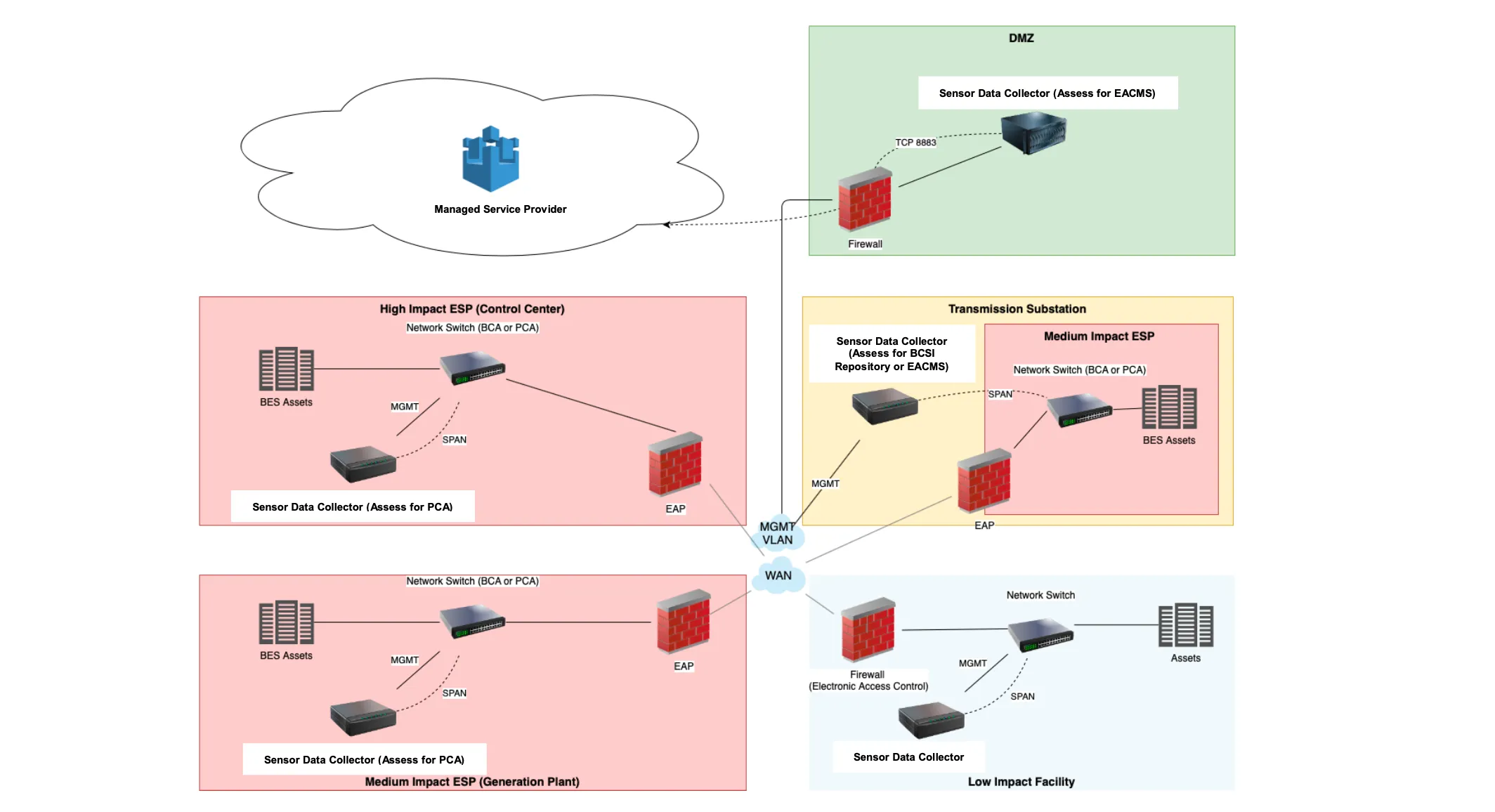
The ERO Enterprise CMEP Practice Guide for Network Monitoring Sensors, Centralized Collectors, and Information Sharing also supports BCSI classification:
The North American Transmission Forum (NATF) has also supported the BCSI classification in its INSM Implementation Guidance.
The entity must evaluate the INSM system against their CIP-002 and CIP-011 processes to determine if the system could be considered an EACMS or a BCSI repository.
When to Consider the EACMS Classification
An EACMS classification carries the lowest asset classification audit risk but the highest compliance overhead. EACMS assets have the most applicable requirements among the three options. Additionally, an EACMS outside the ESP will likely contain BCSI information, resulting in additional requirements. The EACMS designation offers the most location flexibility, as it can exist within or outside the ESP.
An INSM system functions as an EACMS
INSM systems monitor network traffic at the ESP boundaries or within ESPs. This traffic will include access attempts, malicious code or other possible EACMS requirements. If the INSM captures this network activity, it should be considered an EACMS.
In CIP-005-7 and CIP-002-5.1a, NERC defines EACMS broadly to include systems that either control or monitor access. This includes intrusion detection systems and similar monitoring technologies:
- CIP-002-5.1a includes “Electronic Access Points, Intermediate Systems, authentication servers, security event monitoring systems, and intrusion detection systems.”
- CIP-005-7 includes “firewalls, authentication servers, and log monitoring and alerting systems.”
NERC, ERO and industry support for EACMS classification
The CIP-015-01 drafting team provided support for the EACMS classification in the Technical Rationale as part of the Project 2023-03 INSM deliverables.
The ERO Enterprise CMEP Practice Guide for Network Monitoring Sensors, Centralized Collectors, and Information Sharing also supports EACMS classification:
If the sensor performs certain electronic access and/or access monitoring activity, CMEP staff should assess it as possibly an Electronic Access Control or Monitoring System (EACMS) and be subject to the requirements associated with the particular impact level.
The NATF INSM Implementation Guidance supports the EACMS classification.
When to Consider the PCA Classification
If the INSM system is within the ESP, it can be classified as a PCA, resulting in significantly less compliance overhead than an EACMS. A PCA will be subject to the requirements associated with the highest-impact level of the BCSs that it is associated with under the high-water mark principle.
An INSM system functions as a PCA inside the ESP
Inside the ESP, the INSM would not be a BCSI as this classification only exists outside the ESP. An INSM does not function as an EACMS as outlined earlier. This results in the INSM system being best classified as a PCA.
NERC and ERO support for PCA classification
The CIP-015-01 drafting team provided support for the PCA classification in the Technical Rationale as part of the Project 2023-03 INSM deliverables.
The ERO Enterprise CMEP Practice Guide for Network Monitoring Sensors, Centralized Collectors, and Information Sharing also supports PCA classification.
If the sensor is connected using a routable protocol within or on an Electronic Security Perimeter (ESP), CMEP staff should assess whether it should be categorized as a Protected Cyber Asset (PCA), as that term is defined in the NERC Glossary, and the requirements associated with the particular impact level would apply.
Nozomi Support
Nozomi Networks provides an INSM solution that can function under any NERC CIP classification. It ensures that gathering compliance evidence is as efficient and straightforward as possible, reducing time spent on efforts that our platform automatically generates and supplies evidence by default.
Get Your INSM System Classification Right
Classifying your INSM system correctly is not just a compliance checkbox; it’s foundational to meeting CIP-015 INSM requirements and maintaining NERC CIP compliance. The classification you choose will determine the scope of controls, documentation and ongoing maintenance obligations. Here are three steps you can take now to ensure you’re on solid ground:
- Review your INSM architecture, data flows and functions within the context of your NERC CIP program.
- Document your classification rationale to withstand audits and justify compliance decisions.
- Engage expert guidance to ensure your approach aligns with regulatory expectations and industry best practices.
Nozomi Networks can help you navigate these complexities with tailored recommendations and hands-on support. Contact us today to schedule a conversation with one of our NERC CIP experts and strengthen your INSM program.










