フォーブズ誌によれば、2025年はサイバーセキュリティの分水嶺となった。この年、人工知能(AI)が盾と剣の両方となり、防御側と攻撃側のサイバー戦場における関わり方を再定義したのである。攻撃側は今やAIを活用して適応型で自己学習する攻撃を展開し、防御側は機械並みの速度で検知と対応で応戦している。
見出しにはならないが同様に重要な点:長年「パイロット段階の停滞」に陥っていたデジタル変革の取り組みは、クラウドコンピューティング、AI、IoT 5G接続が成熟段階と価格帯に達した2025年に本格化。これにより大規模で手頃な価格のイノベーション推進が可能となった。今日では、OT、IoT ITの融合による業務効率化とジャストインタイム生産の実現が、世界中の大規模産業組織においてほぼ普遍化している。
偶然ではないが、2025年はCISO(最高情報セキュリティ責任者)によるリスク統合の観点で、OT 転換点となった。フォーティネットの調査によると、調査対象組織の過半数(52%)OT 責任をCISO/CSO(最高セキュリティ責任者)に委ねており、2022年のわずか16%から増加している。 企業リスクの責任者として、CISOはデータ完全性と可用性の保護だけでなく、サイバー・フィジカルレジリエンスの確保を目的とした包括的戦略を実行し、その進捗を取締役会に明確に説明しなければならない。サイバーセキュリティリスクを統合する規制圧力もこの傾向を加速させている。
IoT 責任を新たに担うCISOであれ、統合されたばかりのSOCでIoT 分析に奔走するアナリストであれ、新たなサイバーセキュリティ対策と安全・効率性の懸念を両立させる方法に悩むプラントオペレーターであれ、産業用サイバーセキュリティの習得曲線は急峻です。特にAIが関与のルールを変えつつある今、その難易度はさらに高まっています。
本記事では、IoT 基礎を解説した後、AIを活用してレジリエンスを構築するための3つの重要な方法について説明します:
- エンドポイントおよび無線センサーによる100%の資産可視性
- 点と点を結びつける包括的なthreat intelligence
- OT スキルギャップを解消するSOC効率性
OT IoT:企業サイバーリスクの最も急速に成長する要因
業界を問わず、OT IoT デジタル資産全体に占める割合が増加している。2024年の調査によると、OT、IoT その他の専門システムは企業資産の42%を占め、中~高レベルの企業リスクの64%を占めている。 言い換えれば、企業の攻撃対象領域で最も急速に拡大している部分は、CISOが最も理解しておらず、最も投資が不足している領域である。なぜならITサイバーセキュリティツールIoT 機能しないからだ。この急拡大は主要ステークホルダーからの疑問を招いている。
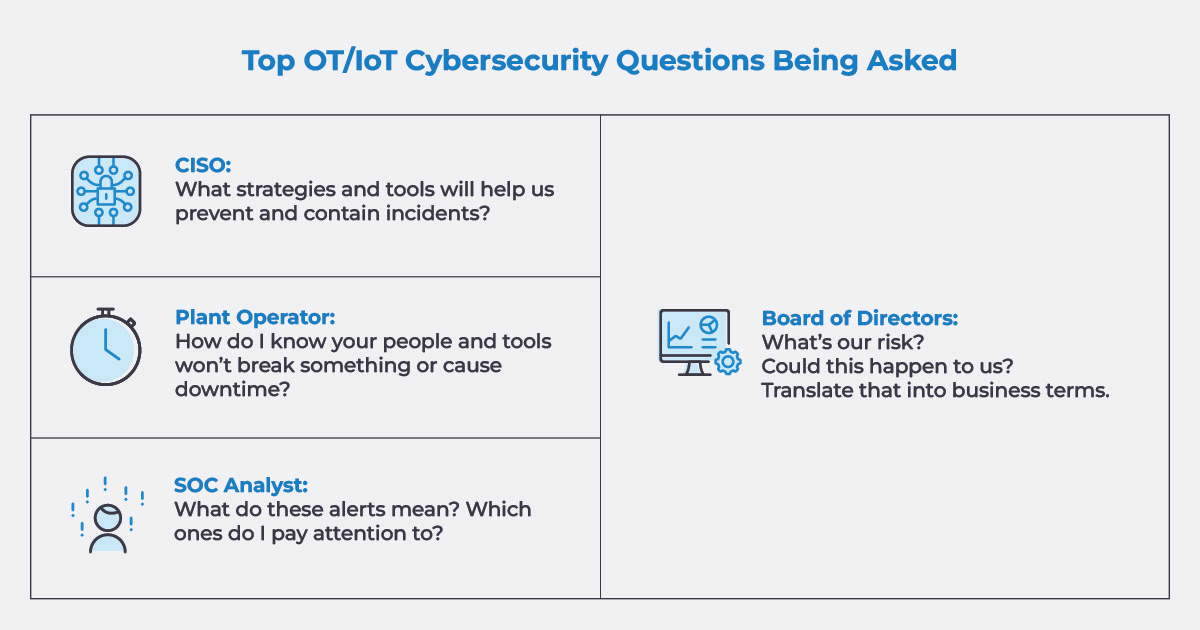
これらの疑問を生じさせる差異は以下の通りです。
OT ITセキュリティとどう違うのか?
OT 、「OT 」と言われることにうんざりしているでしょう。またOT 、その違いを説明することに疲れているはずです。細かい違いは数多くありますが、OT 異なる主な点、そしてITセキュリティツールが機能しない理由を以下に示します。
- 物理的影響。ITは情報を管理する。OT 収益を生み出す中核資産や重要な公共サービスを提供する物理的プロセスをOT 。多くの場合、これらは継続的に稼働している。OT 攻撃を受けた場合、特に重要インフラにおいては、その影響はより深刻となる。
- サイバーセキュリティの目標。ITセキュリティは機密性、完全性、可用性(CIAトライアド)を重視する。OT プロセスの稼働時間、安全性(人的・環境的)、信頼性を重視する。
- 標準的なものは何もない。ITソリューションは標準的なOSを使用し、頻繁に自動更新が行われ、3~5年ごとにアップグレードまたは交換される。OT ~15年使用することを前提に設計されており、「設計上不安全」である。パッチは提供されても頻度が低く、更新はメンテナンス期間中に実施しなければならない。
ITセキュリティツールが機能しない理由は、数百ものOT 読み取れず、ディープパケットインスペクション(DPI)を実行できず、異常を検知するための正常動作のベースラインを確立できないためである。さらに、アンチウイルス保護やパッチ適用で標準的なITエンドポイントエージェントはOT では機能しない。これらは重く、業務を妨げ、OT 向けに訓練されていないため、誤った脅威を検知してしまう。
IoT ITセキュリティとどう違うのか?
モノのインターネット(IoT )とは、データを収集・共有・活用して現代社会を円滑に機能させる、インターネット接続デバイスの生態系である。IoT 至る所に存在し、OT と同様に、設計上通常はセキュリティ対策が不十分である。追加的な課題により、OT セキュリティアプローチが求められる。例えば:
- 多様なデバイスの急増。 無線接続の多くIoT 、その 数と種類が 拡大を続け、簡素化されたOSと互換性のないプロトコルを使用し、しばしば臨機応変に導入される。
- 設計上、管理不能かつ不安全。一度導入されると忘れ去られ 、暗号化もパッチ適用不可のファームウェアを備えたインターネットに晒されたデバイスは、境界防御を迂回する理想的な足掛かりとなる。
- 脆弱なIDおよびアクセス制御。 デフォルトパスワードの使用 や、リモートアクセスを含む強力な認証手順の欠如により、IoT 悪用されやすくなっている。
多様なIoT (その多くは無線接続)の膨大な数と、脆弱あるいは存在しないセキュリティ対策が相まって、従来のITセキュリティツールは効果を発揮できない。
新たな資産インベントリ:ワイヤレスとエンドポイントを見逃すな
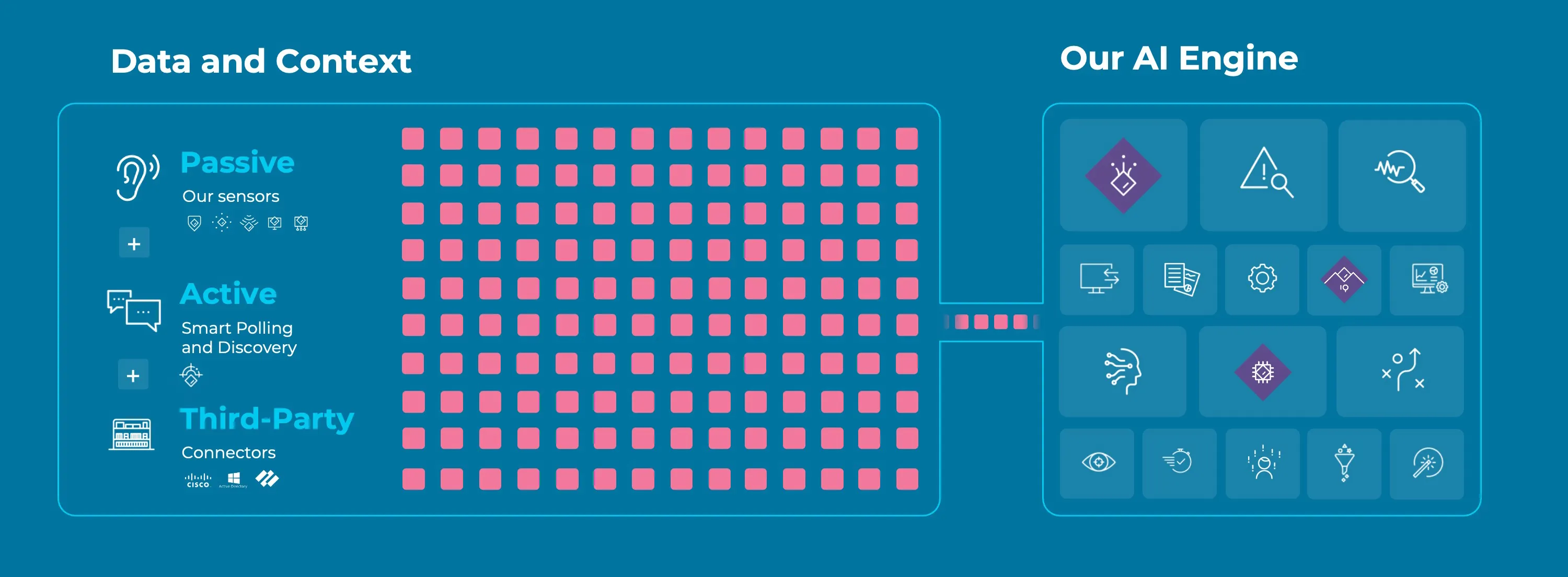
資産の可視性。資産の棚卸し。資産管理。名称はともかく、保有資産を把握することは、あらゆるサイバーセキュリティフレームワーク、規制、プログラムの基盤です。効果的な異常検知、脆弱性管理、そして最終的にはリスク管理の出発点となります。DPIを用いたSPAN/TAP経由の有線ネットワークトラフィックの受動的監視は、OT 標準でした。しかし、もはやそれだけでは不十分です。
2026年、OT、IoT IT資産の完全かつ自動化されたインベントリが必要となります。これには、それらの動作と通信に関する深い洞察が求められます。実現には、エンドポイントから空中までのセンサー、受動的・能動的なデータ収集、IoT 精通、サードパーティのIT資産データの組み合わせが必要です。AIを活用し、デバイス照合に基づいて不足する詳細情報を補完することで、それらのリスクを把握できるようになります。
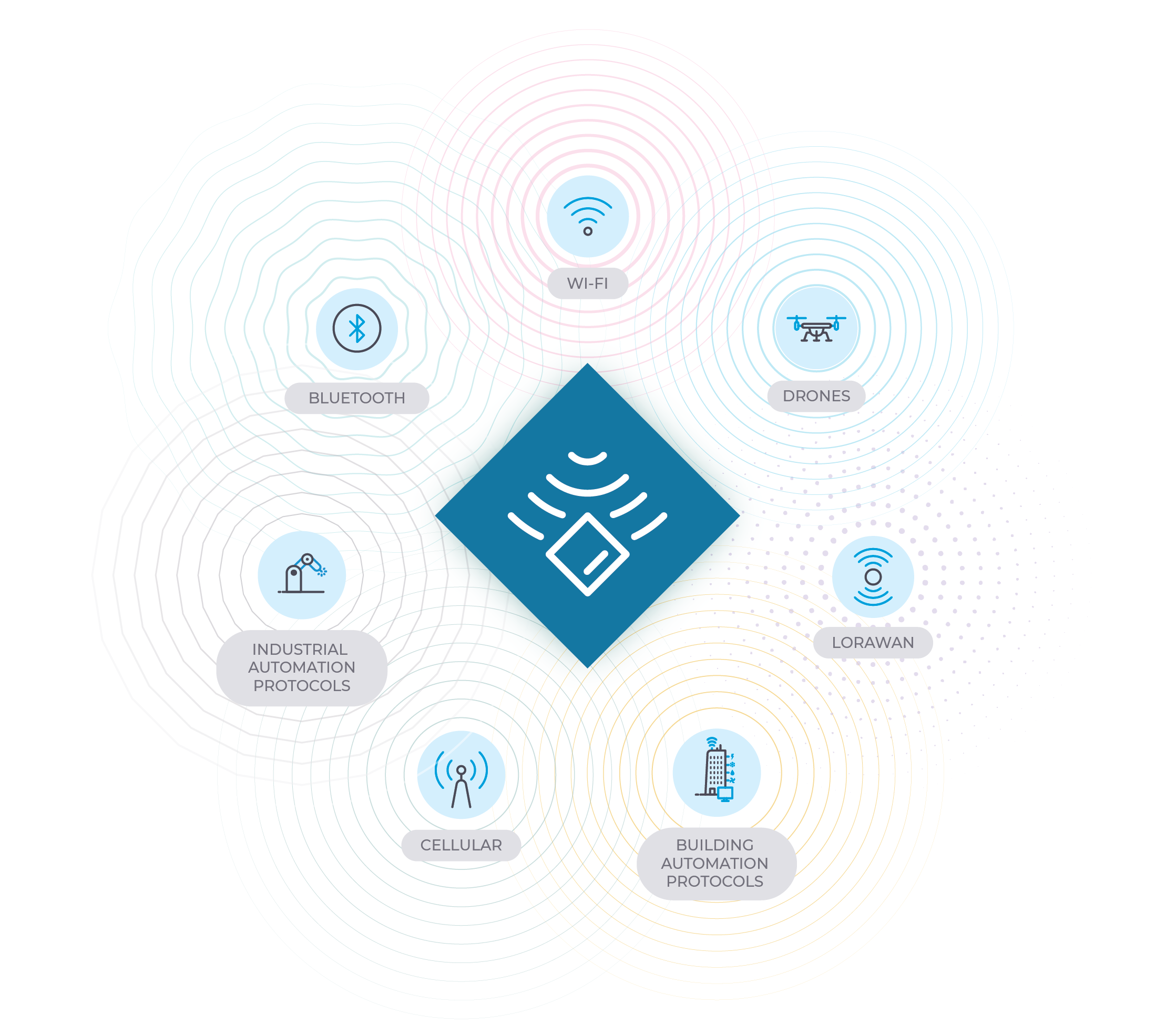
ワイヤレスセキュリティセンサー
産業組織は物流、自律輸送、監視において無線通信への依存度を高めているが、成熟した組織でさえ、これらが最大の盲点となるケースが多い。 無線通信デバイスの断続的な動作は、正常動作のベースライン設定をさらに困難にする。IoT センサーIoT Bluetoothやセルラー通信に加えLoRaWANやODIDといったプロトコルを読み取り、認証解除攻撃(deauth attack)、不正無線アクセスポイント(WAP)、侵害された認証情報を利用した無線ネットワーク侵入といった無線脅威を検知できる。
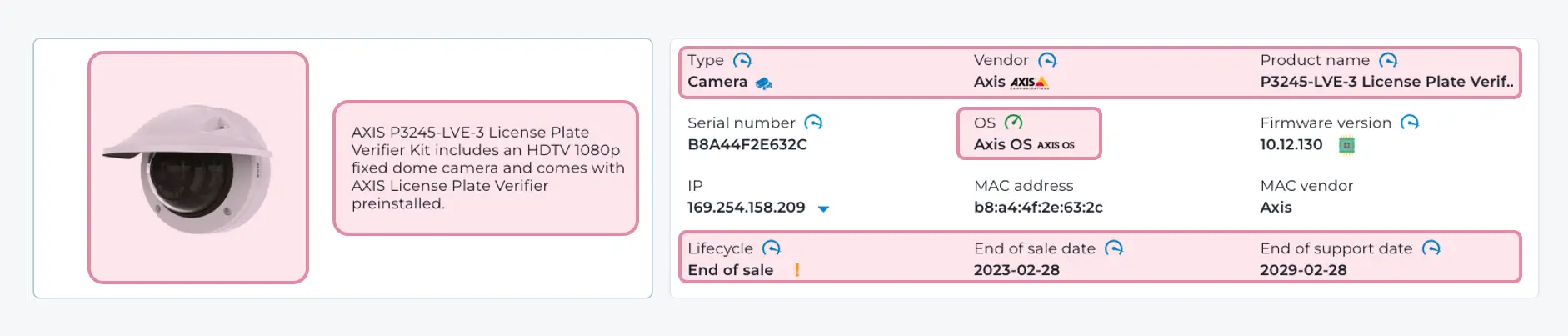
エンドポイントセキュリティセンサー
ITセキュリティ分野では、エンドポイントエージェントはウイルス対策やパッチ適用に広く普及しているが、OT への導入における否定的な経験から、採用は限定的である。専用設計OT センサーはこうした懸念を解消するが、資産情報の収集だけでは不十分だ。誰が、いつ、どのマシンにログインしたかを検知する機能も必要である。 ヒューマンインターフェースデバイス(HID)、ヒューマンマシンインターフェース(HMI)その他のデバイスは、人(遠隔地の第三者技術者を含む)が操作する場所であり、したがって不審な活動が発生する場所でもある。
AIを活用した資産マッチング
AIは資産プロファイルを充実させ、資産インベントリの精度をほぼ100%に高めるために不可欠です。トラフィックパターンから資産の種類や役割を推測し、対応するデバイスから豊富な詳細情報を活用して欠落データフィールドを補完することで、センサー収集データを強化します。こうしたギャップを埋めることで、既知の悪用された脆弱性(KEV)を持つ資産など、リスクの高い資産を特定するための重要な情報に焦点を絞ることが可能になります。
IT、IoT OT 網羅Threat Intelligence 実用的なThreat Intelligence
産業環境に影響を与える攻撃の大半は、ITシステムへの侵害から始まり、OTへ展開します。ITthreat intelligence 情報セキュリティの基盤ですが、侵害がOT IoT に及ぼす下流の影響を検知することはできません。現代の産業・重要インフラ環境はOT、IT、IoT 複合に依存しているため、これらを監視する脅威検知ツールには、高品質で包括的な脅威インテリジェンスの継続的な供給が不可欠です。 threat intelligence。セキュリティ対策が不十分で管理されていないインターネット接続IoT 、ハクティビストの好む攻撃ベクトルである。OTへの直接攻撃は比較的少ないものの、高度な持続的脅威グループや地政学的緊張の高まりにより増加傾向にある。
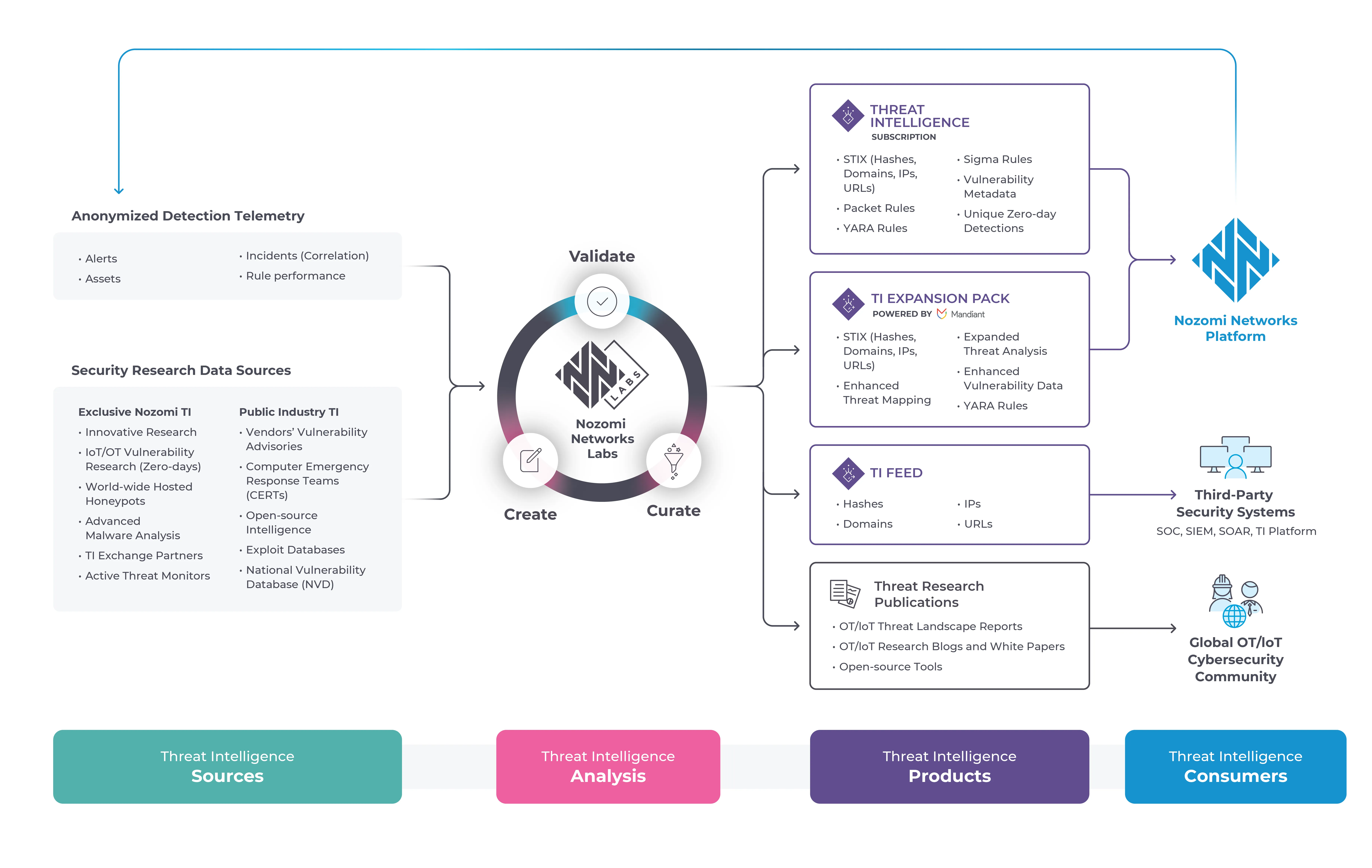
点と点を結ぶ厳選インサイト
資産の可視化が静的なデータベースやIPアドレスのリストだけでは不十分であるのと同様に、threat intelligence 侵害の兆候(IOC)の生データフィード以上のthreat intelligence 脅威検知ツールの性能は、threat intelligence 質に依存する。Yaraルール、パケットルール、Sigmaルールといった詳細情報に加え、OT IoT に特化したSTIXや脆弱性指標が必要である。この用語が示す通り、産業環境を標的とする脅威アクターの行動や戦術に関する実用的な知見を提供できるよう、インテリジェンスは厳選されるべきである。
すべてをパッチ適用できない場合の脆弱性リスク評価
ITには「パッチ・チューズデー」がある。OT IoT「パッチ・ネバー、ネクスト、ナウ」だ。全てにパッチを適用できるわけではなく、時には全く適用できない場合もある。これが脆弱性管理をはるかに困難にしている。修復の優先順位付けにはAIを活用したリスクスコアリングが不可欠だ。KEV(重要脆弱性)の特定に加え、資産の重要度、露出度、既に実施されている制御策も考慮に入れることができる。
SOC効率性:OT のギャップを解消する
「簡単ボタン」が必要なのは、OT IoT に不慣れで圧倒されているSOCアナリストに他ならない。 資産インベントリから行動ベースライン設定、脅威・異常検知、脆弱性管理に至るまで、サイバーセキュリティプラットフォームのあらゆる側面にAIが浸透するとき、それらの機能はSOCで結実する。最も重要な情報が可視化され、アナリストが重大な問題を逃さないようにするためだ。単に表示されるだけでなく、継続的に更新され、相関分析され、リスクに応じて優先順位付けされ、さらに深い洞察や次のアクションへのドリルダウンアクセスが提供される。
数千ものデータポイントをレビューし、関連付け、優先順位付けするという煩雑な作業を、疲れを知らないAIエンジンに委ねることで、Tier 1 SOCアナリストやその他のジュニア職を完全に不要にできる可能性があります。重要度の高い数件のアラートをノイズの中から探し出す必要はもうありません。単なる1件のアラートへの対応だけでなく、全体的なリスクを最小限に抑えるための行動方針に迷うこともなくなります。
こんにちは、環境について何でも聞いてください
デジタルアシスタントが普及したのは、平易な言語で質問した際に、そうでなければ何時間も調査が必要だったであろう回答を即座に提供するためだ。 SOCアナリストが商用チャットボットに助けを求めているのは間違いないが、信頼できる回答を得るには、OT IoT 、環境で起きていることに基づいて文脈に沿って応答できるAIアシスタントが必要だ。例えばNIS2やIEC 62443要件といった一般的なコンプライアンス質問をする代わりに、自社の特定環境が準拠しているかどうか、準拠していない場合は何をどの順序で実行すべきかを尋ねられるようになる。
AIは広範である。あらゆるユースケースに適した種類を活用せよ。
サイバーセキュリティ侵害やその他の失敗は、組織が見えないもの、知らないもの、あるいはさらに悪いことに保護されていると誤って想定しているものから圧倒的に生じている。これらの盲点が相まってサイバーリスクを高めている。攻撃対象領域の拡大と制御不能なAI駆動型脅威の間で、侵害を完全に防ぐことはますます困難になっているが、ここで説明するAI駆動型戦略とツールを活用すれば、ギャップを埋め回復力を構築する手段は十分に手の届く範囲にある。
AI搭載IoT プラットフォームには、APIで接続した市販のチャットボットやLLMを単に追加しただけでは不十分である。
2025年、ChatGPTやCopilotのような生成AIツールが広く普及し、AIの力を誰もが手にできるようになった。しかし、大規模言語モデル(LLM)に依存して「思考」するこの限定的なAIを、他のモデルと混同するのは誤りである。IoT プラットフォームが真にAI駆動となるには、商用チャットボットやLLMをAPIで接続しただけのものよりもはるかに高度な機能が必要だ。
脅威アクターは多種多様なAIを活用し、これまで以上に迅速に高度な攻撃を仕掛けています。サイバー防御側も同様に、適切なAI手法を正しく活用し、少なくとも脅威のペースに追いつく必要があります。Nozomi Networks 具体的な運用例をご覧になりたい方は、デモをご請求ください。












