AutomationDirect is a well-established PLC vendor whose products are used across industries such as food and beverage, amusement parks and water/wastewater utility systems. Their Productivity PLC series offers a scalable line of controllers, from compact stackable micro-units (Productivity1000) to high-capacity modular systems (Productivity3000).
These devices are programmed using Productivity Suite, free software developed and distributed by AutomationDirect. The suite supports IEC 61131-standard languages, such as Ladder Logic, enabling control engineers to program and monitor Productivity PLCs.
Because engineering workstations are often connected to both IT and OT networks, they present an attractive target for attackers. For this reason, Nozomi Networks Labs analyzed the Productivity Suite software, which runs on these workstations, and identified nine vulnerabilities. These flaws allow unauthenticated remote attackers to read arbitrary files from a workstation and, if a control engineer is tricked into opening a malicious project file, to fully compromise the machine.
All findings were responsibly disclosed to AutomationDirect, which responded quickly and released fixes in the latest version of Productivity Suite (4.5.x.x).
This article details the identified vulnerabilities, their potential impact, possible attack scenarios, and recommended mitigation strategies. For a full list of affected devices and versions, see the section “Vulnerability List and Affected Versions”.
Research Scope

AutomationDirect, founded in 1994 as one of the first online PLC shops, sells affordable automation hardware directly to customers. By cutting out middlemen, the company built a reputation for delivering cost-effective PLCs and control products backed by solid technical support.
Productivity PLCs (Figure 1) are AutomationDirect’s family of controllers designed for a wide range of industrial automation applications. They are used by manufacturing companies, OEMs, and system integrators who need reliable and cost-effective PLCs to control production lines, packaging equipment, material handling systems, and other factory processes.

The controllers are programmed with Productivity Suite (Figure 2), a free Windows-based development environment. The Suite supports IEC 61131 languages such as Ladder Logic, combines multiple programming views in a modern workspace, and includes a built-in PLC Simulator for offline testing. It also provides the option to encrypt project files for protection and allows engineers to define user roles for each project (e.g., admin, read-only access).
All the security flaws discussed in this blog were identified through an analysis of the Productivity Suite software.
これらの脆弱性の影響
The 9 vulnerabilities identified on the Productivity Suite presented substantial security implications for the industrial environment. Below are some examples of possible attack scenarios that could arise from the exploitation:
- Loss of Productivity and Revenue (T0828): Vulnerabilities CVE-2025-62498, CVE-2025-61977 and CVE-2025-62688 allow attackers to tamper project files so that, if a control engineer opens them, the attacker gains full control over the workstation. From there, the attacker can interact with the OT network and potentially reprogram all connected PLCs. This attack still works on encrypted projects and with only low-privileged credentials making it especially dangerous, as encryption can create a false sense of safety.
- Theft of Operational Information (T0882): Vulnerabilities CVE-2025-61934 and CVE-2025-58456 enable unauthenticated attackers with network access to a workstation running Productivity Suite to interact with the PLC simulator and download arbitrary files. Stolen files could include PLC project files, browser cookies, or any other sensitive data saved on the machine by control engineers.
- Denial of Control (T0813): Vulnerabilities CVE-2025-61934, CVE-2025-58429 and CVE-2025-60023 enable unauthenticated attackers with network access to a workstation running Productivity Suite to interact with the PLC simulator and delete files or write arbitrary content to the workstation’s filesystem. This could effectively brick the engineering workstation, blocking engineers from monitoring or changing PLC configurations.
脆弱性リストと影響を受けるバージョン
The following table list all the vulnerabilities Nozomi Networks Labs has found on the AutomationDirect Productivity Suite version up to and including 4.2.3.2 during this vulnerability research:
脆弱性スポットライト
After analyzing the vulnerabilities, we outlined an attack scenario in which unauthenticated attackers with network access to a workstation running Productivity Suite could steal sensitive data (e.g., browser cookies, PLC projects), gain full control of the workstation, and from there compromise the OT network.
The vulnerabilities involved in the attack chains are the following.
PLC Emulator Issues: CVE-2025-61934 and CVE-2025-58456
The Automation Studio software running on workstations includes a feature that lets engineers simulate a PLC and test project code without uploading it to a physical device. The emulator starts automatically when the workstation launches, requiring no action from the operator.
The emulator locally replicates the Productivity PLC protocol, a proprietary UDP-based protocol developed by AutomationDirect, allowing the workstation to interact with it as if it were a real device. It also implements the same PLC discovery protocol, meaning it responds to broadcast requests and can be easily identified on the network.
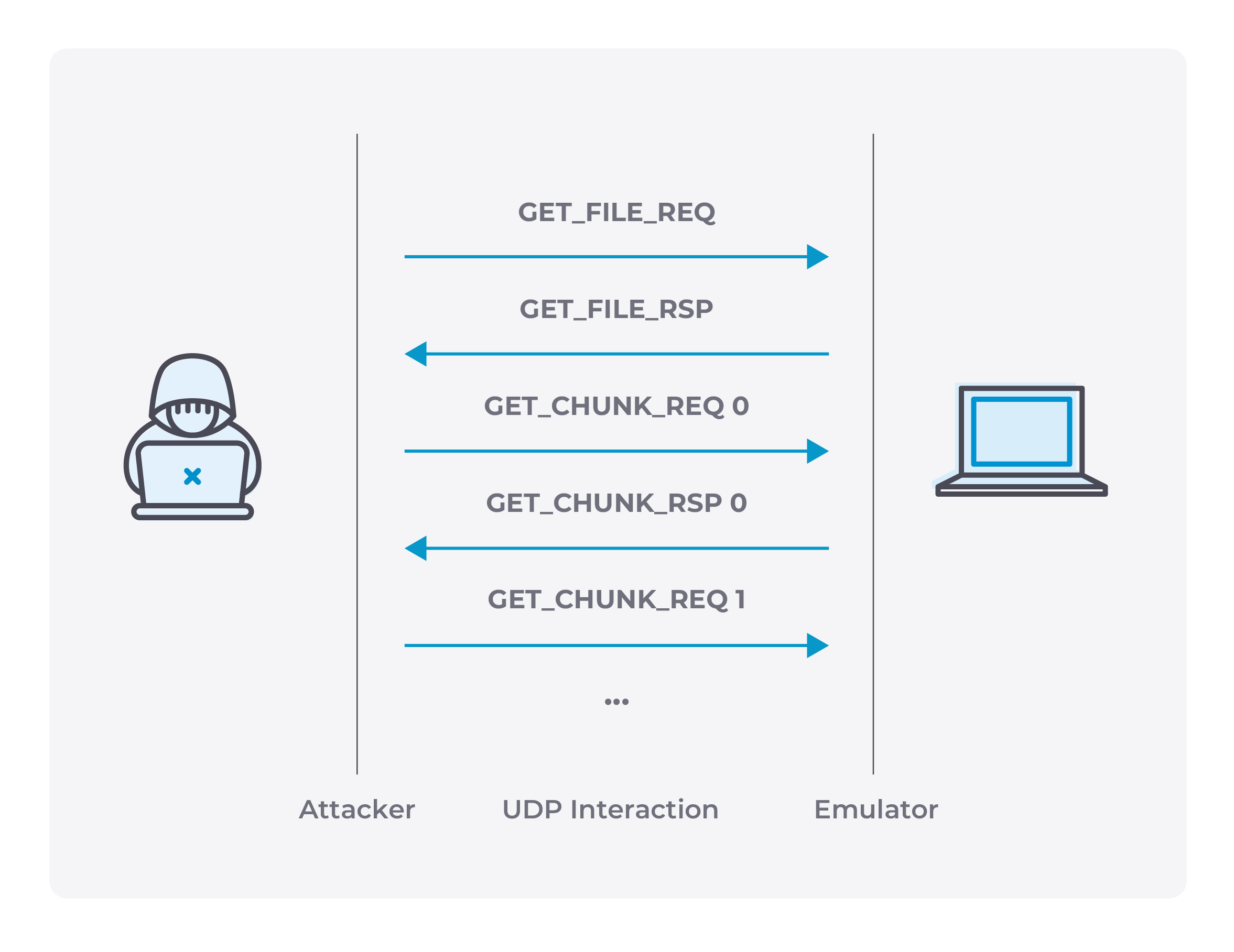
The first issue (tracked as CVE-2025-61934) is that anyone with network access to the workstation can interact with the emulator, since it binds to every network interface. Because the Productivity protocol lacks authentication, an attacker can connect remotely and use it to upload, download, or delete files and folders on the workstation.
Normally, the emulator restricts interactions to files stored in a temporary directory. However, due to CVE-2025-58456, the software fails to prevent directory traversal during downloads, allowing an attacker to access files outside the temporary directory. As a result, an attacker can download any file from the workstation over the network without authentication.
When chained together, these two vulnerabilities are critical: attackers can exfiltrate browser cookies, PLC projects, and other sensitive information stored on the device via network and without any authentication.
The diagram below shows a schematized interaction between the attacker and the emulator service on the workstation during file download.
Project Format Issues: CVE-2025-62498 and CVE-2025-61977
A Productivity Suite project file is a binary file with the following structure:
Productivity Suite project file header structure – Encryption off
If encryption is not enabled, the least significant bit of the flags field is set to zero, and the DATA portion at offset 4 contains a ZIP file. This ZIP file stores all the XML files that define the Ladder Logic program and related metadata used by Productivity Suite to load the project, as shown below:
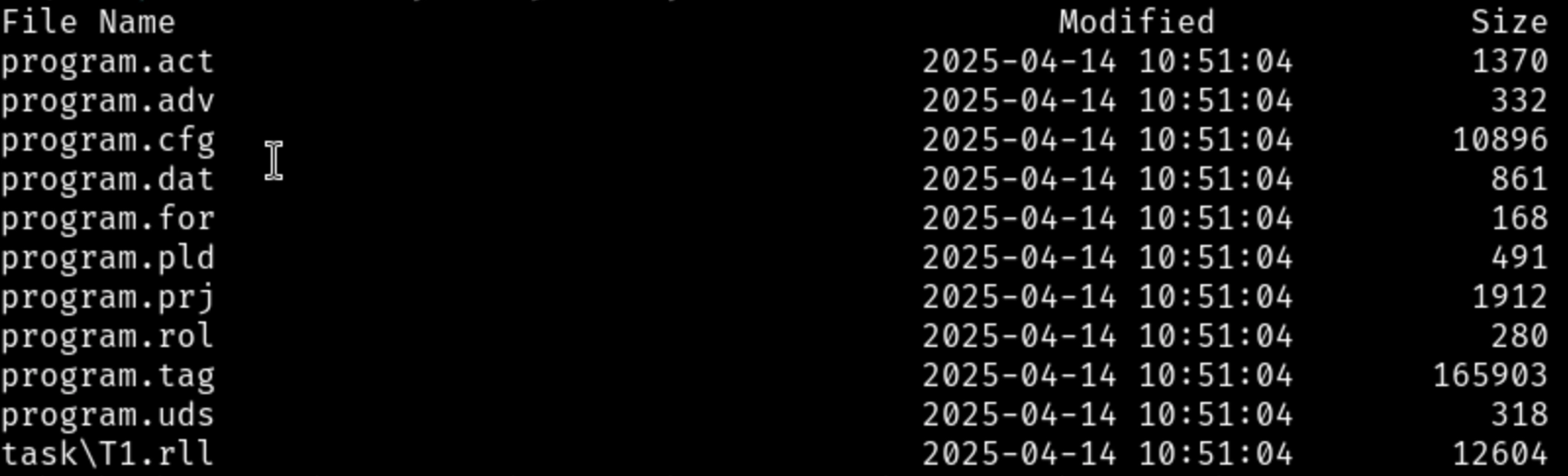
A first issue (tracked as CVE-2025-62498) is that the decompression routine is vulnerable to a ZipSlip flaw, which allows extraction of files with relative paths. This enables attackers to embed files that are written into arbitrary directories on the workstation, effectively granting arbitrary file write access.
With this primitive, an attacker can create files that executes on the workstation, achieving arbitrary code execution. For example, they could place a file in:
C:\Users\USERNAME\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup
If the project is encrypted, however, the above attack cannot be executed directly, since the attacker cannot decrypt the project. Let’s take a closer look at how project encryption works.
The Productivity Suite allows projects to define users, which changes the file structure as follows:
Productivity Suite project file header structure – Encryption on
The least significant bit of the flags field is set to one, and at offset 6 the project contains an XML file encrypted with a hardcoded key. This XML file stores metadata about the users defined in the project. The ZIP file is then stored in encrypted form at offset XML_SIZE+6.
The ZIP file is encrypted with a master key, which is saved multiple times in the XML file, each instance encrypted with either the password of a defined user or, if security questions are enabled, the answer to one of those questions.
The issue (tracked as CVE-2025-61977) is that the master key can be retrieved by answering only one security question of any user. Since answers to security questions are typically weaker than passwords and no complexity policy is enforced, the likelihood of a successful guess is high.
Thus, by brute-forcing a password or guessing the answer to a security question, an attacker can decrypt the ZIP, tamper it, and then exploit the ZipSlip vulnerability to embed malicious files into arbitrary directories on the workstation.
Tampering an encrypted project is particularly dangerous because control engineers are more inclined to trust its contents. As a result, they may open the project without realizing it has been compromised, especially since a tampered project appears identical to a legitimate one.
Attack Scenario

Figure 3 outlines an attack scenario against an OT network accessible from a workstation running Productivity Suite. The attacker first requires access to a network connected to that workstation. From there, they can exploit CVE-2025-61934 and CVE-2025-58456 to discover running emulators and exfiltrate sensitive information, such as browser cookies, PLC projects, credentials, configuration files, and other data stored on the workstation.
The exfiltration step itself is highly impactful. Stolen browser cookies and credentials can let an attacker impersonate users, access web-based management consoles, or escalate privileges on other systems. PLC projects and configuration files reveal control logic, network topology, and device settings, information that can be used to plan precise operational disruptions or to craft convincing targeted lures. Even if the attacker stops after exfiltration, the consequences (data leakage, operational sabotage, IP theft, safety risks, and regulatory exposure) can be severe.
If the attacker chooses to continue, they can then leverage CVE-2025-61977 and CVE-2025-62498 to decrypt the exfiltrated project files and modify them to include a malicious payload that executes on the workstation when a control engineer opens the project. They can also modify PLC code that will later be deployed to the controllers.
To deploy this attack, the attacker may run a phishing campaign to trick a control engineer into opening the tampered project. Once opened, the workstation becomes infected, allowing the attacker to move into the OT network and reprogram connected PLCs with severe consequences for industrial operations.
For example, in a food-and-beverage factory, an attacker exploiting this chain could:
- Stop the production line causing economic loss
- Introduce a malfunction on the packaging line that causes the spoilage of the food produced
修復
AutomationDirect has addressed these vulnerabilities through security patches for the Productivity Suite software. A security report has been published by CISA: https://www.cisa.gov/news-events/ics-advisories/icsa-25-296-01. Asset owners and operators are strongly urged to:
- Update affected Workstations with the newer version of the Productivity Suite.
- Implement network segmentation to limit exposure of systems.
- Do not trust project files coming from untrusted sources, even if encrypted.
- Monitor network traffic for the presence of vulnerable assets and suspicious activity.
To help organizations promptly identify whether the workstations with the vulnerable software are present in their environment—and to detect and alert on exploitation attempts before they lead to operational disruption, compromise, or further attack progression – asset owners can rely on the advanced capabilities of Nozomi Networks OT/IoT Security Platform. The platform provides deep visibility into network traffic and host activities, enabling effective vulnerability and threat detection across OT networks.
This proactive monitoring empowers security teams to respond to vulnerabilities and attacks swiftly and effectively, minimizing the impact of attacks targeting critical networks.
To learn more about Nozomi Networks platform and see it in action, request a demo.