The Cognex IS2000M-120 is an industrial smart camera primarily used for machine vision applications such as part inspection, presence detection, and barcode reading in manufacturing and automation environments. It combines imaging, processing, and I/O in a compact, standalone unit designed for easy deployment on production lines.
As part of its ongoing commitment to securing industrial technologies, Nozomi Networks conducted a thorough security assessment of the IS2000M-120. The research uncovered nine impactful vulnerabilities, several of which could potentially allow an attacker to fully compromise the device, posing serious risks to operational integrity and safety in industrial settings.
Despite the fact that the IS2000M-120 remains a commercially available product, the vendor has acknowledged that it is considering an end-of-life status for the device. Consequently, no security patches are planned, leaving users reliant on external mitigation strategies.
In coordination with the Cybersecurity and Infrastructure Security Agency (CISA), a security advisory has been published. This advisory outlines the discovered vulnerabilities and provides practical solutions and mitigation steps to help organizations reduce the risk of exploitation and protect their industrial environments.
リサーチ範囲
The scope of this research focuses on the Cognex In-Sight Explorer ecosystem, a widely used platform for machine vision in industrial automation. At the center of this ecosystem is the Cognex IS2000M-120, a compact smart camera that integrates imaging, processing, and I/O capabilities into a single device. Designed for tasks like part detection and barcode scanning, it operates autonomously in production environments and is often deployed in critical manufacturing workflows.
To manage and configure the camera, users rely on the Cognex In-Sight Explorer client-side software, which serves as the interface for accessing the device. This software enforces authentication and authorization mechanisms, helping control which users can interact with the camera and perform sensitive operations such as modifying configurations or retrieving data.
Communication between the client software and the camera takes place over the proprietary Cognex In-Sight protocol, a custom protocol used for exchanging commands, configuration data, and image results. This protocol plays a central role in the overall security model of the ecosystem, as it governs how control and data flow between the user interface and the device itself.
脆弱性の潜在的影響
The vulnerabilities discovered in the Cognex IS2000M-120 camera have serious implications from three primary threat perspectives. First, an unauthenticated attacker on the same network segment as the device—who is capable of intercepting traffic, for example via a Man-in-the-Middle (MitM) attack—can fully compromise the device through multiple attack vectors. This scenario presents a critical risk in environments where network segmentation or encryption is not enforced. Second, a low-privileged user with limited access to the camera can escalate their privileges by creating a new administrative account and gaining full control of the device, effectively bypassing built-in access controls. Third, if an attacker has limited access to the Windows workstation where the Cognex In-Sight Explorer software is installed, they can manipulate backup data intended for the camera. This tampering can cause the camera to execute unauthorized or malicious tasks, potentially leading to a disruption of service.
From a MITRE ATT&CK® standpoint, this activity corresponds to T1210 – Exploitation of Remote Services, as it involves abusing legitimate remote interfaces to gain unauthorized access. While the camera itself does not store sensitive data nor function as a network infrastructure component, its role in industrial automation processes makes it a critical asset. Exploiting it can cause operational disruptions, impacting physical workflows and potentially leading to production downtime or process errors. Even without targeting data confidentiality or broader network compromise, the consequences of such exploitation can be severe due to the camera’s integration into industrial control systems.
脆弱性リストと影響を受けるバージョン
Nozomi Networks identified these vulnerabilities in the Cognex In-Sight Explorer client software version 6.5.1 and in the Cognex IS2000M-120 camera firmware version 6.5.1. Cognex confirmed the list of affected devices and configurations:
- In-Sight 2000 camera series all firmware versions 5.x and 6.x up to and including 6.5.1
- In-Sight 7000 camera series all firmware versions 5.x and 6.x up to and including 6.5.1
- In-Sight 8000 camera series all firmware versions 5.x and 6.x up to and including 6.5.1
- In-Sight 9000 camera series all firmware versions 5.x and 6.x up to and including 6.5.1
- In-Sight Explorer software all versions 5.x and 6.x up to and including 6.5.1
脆弱性スポットライト
We provide further insight into the vulnerabilities by revisiting the three attack scenarios discussed earlier in this blog.
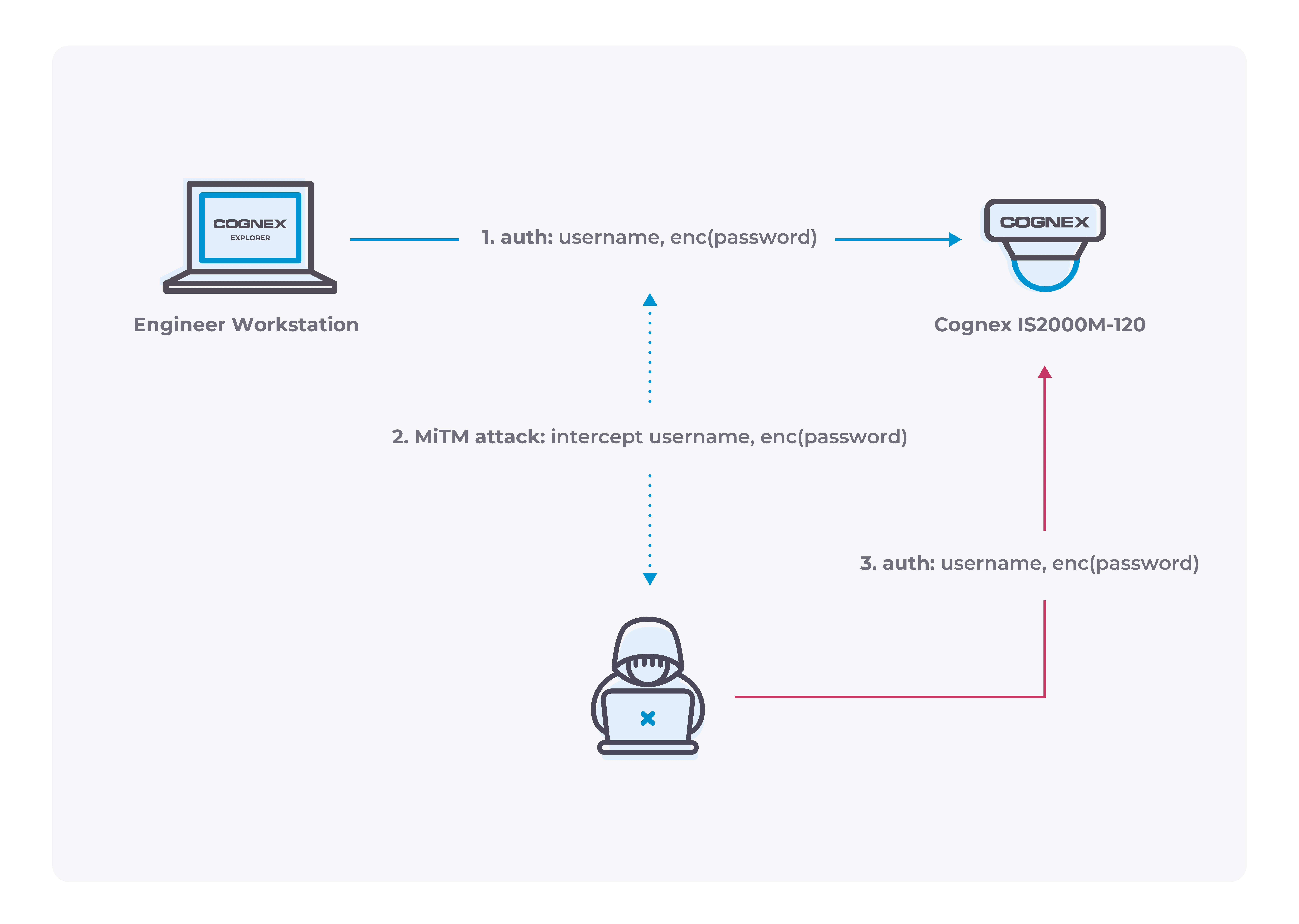
First scenario: An adjacent, unauthenticated attacker with access to the same network segment as the Cognex IS2000M-120 camera can compromise the device by intercepting traffic in a Man-in-the-Middle (MitM) attack. This is possible due to weaknesses in the Cognex In-Sight protocol’s authentication mechanism, which relies on a username and password sent by the client. Although the password is transmitted in encrypted form, it is always encrypted using the same symmetric key, even across different sessions.
This flaw enables a replay attack (CVE-2025-54810), allowing an attacker to capture the encrypted credentials and reuse them to obtain a valid session. The attack is shown in Figure 2. The risk is heightened because the encryption key appears to be hardcoded in the freely downloadable In-Sight client software, making it possible for an attacker to decrypt captured credentials once the key is extracted (CVE-2025-54754) as shown in Figure 3.
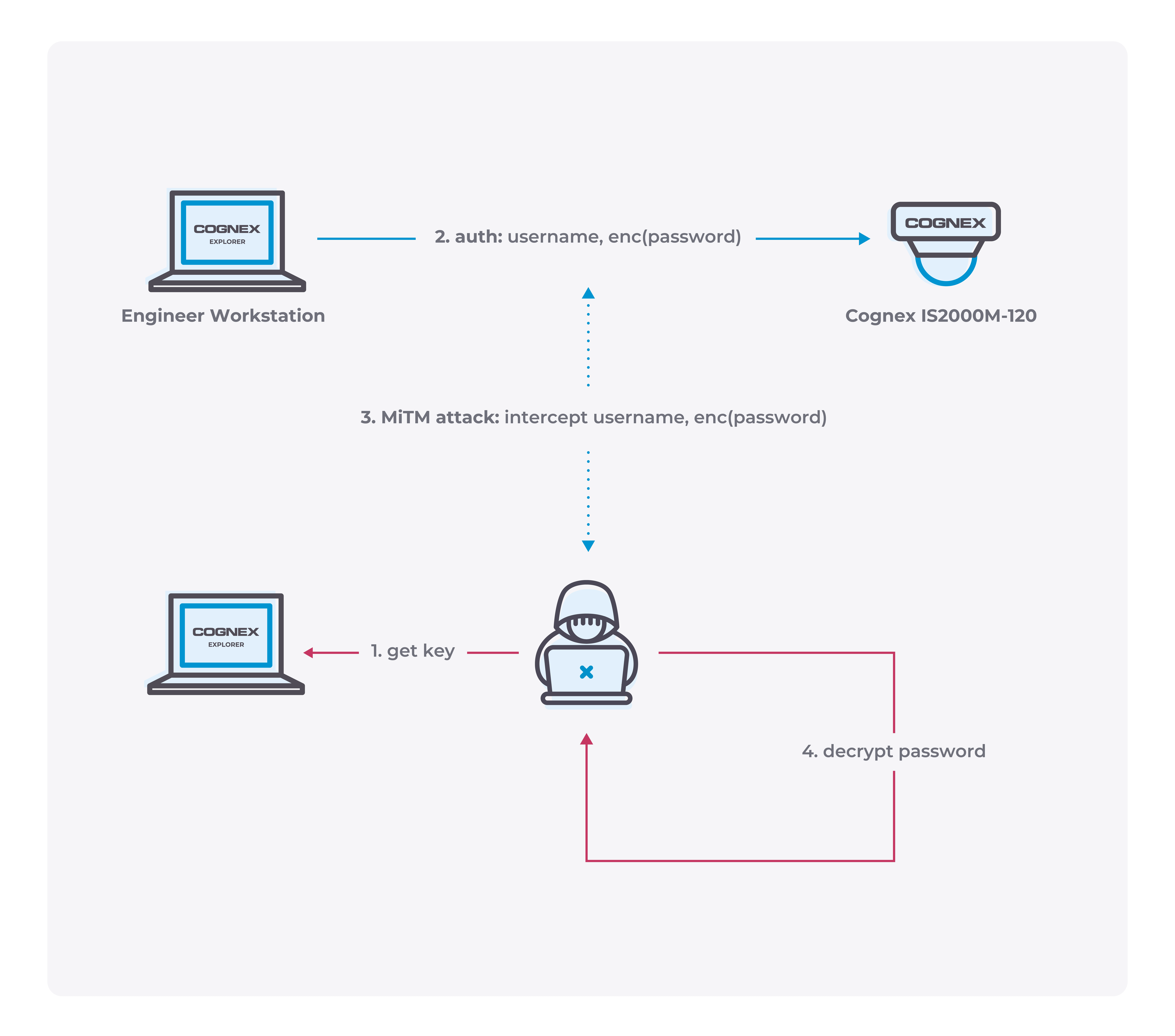
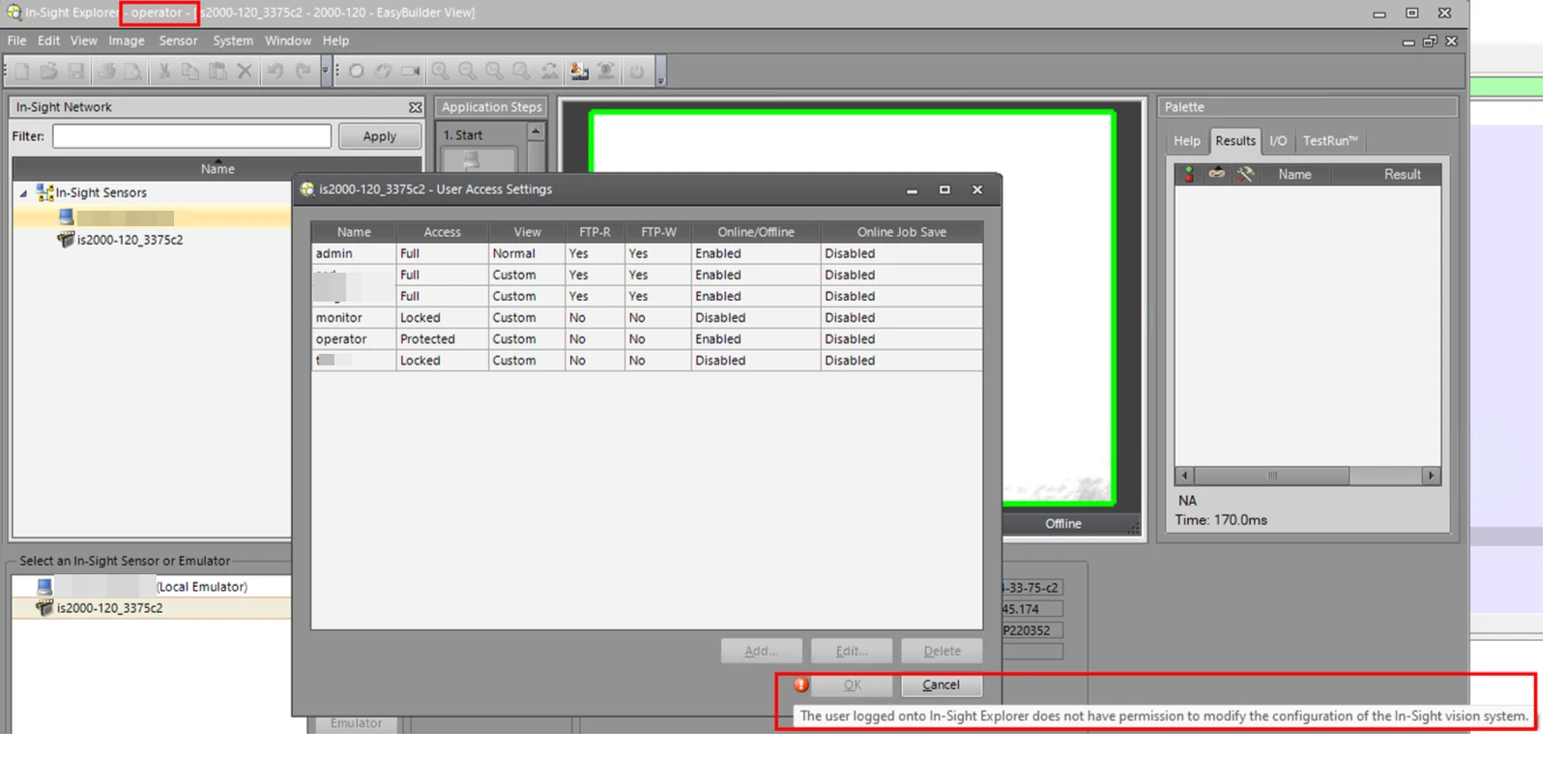
Second scenario: A low-privileged legitimate user can escalate privileges due to improper enforcement of account restrictions. The Cognex In-Sight Explorer software supports three user profiles: full (administrator), protected (limited functions, cannot create/delete users), and locked (no operations allowed). Figure 4 shows a protected-level operator user profile failing to add new users.
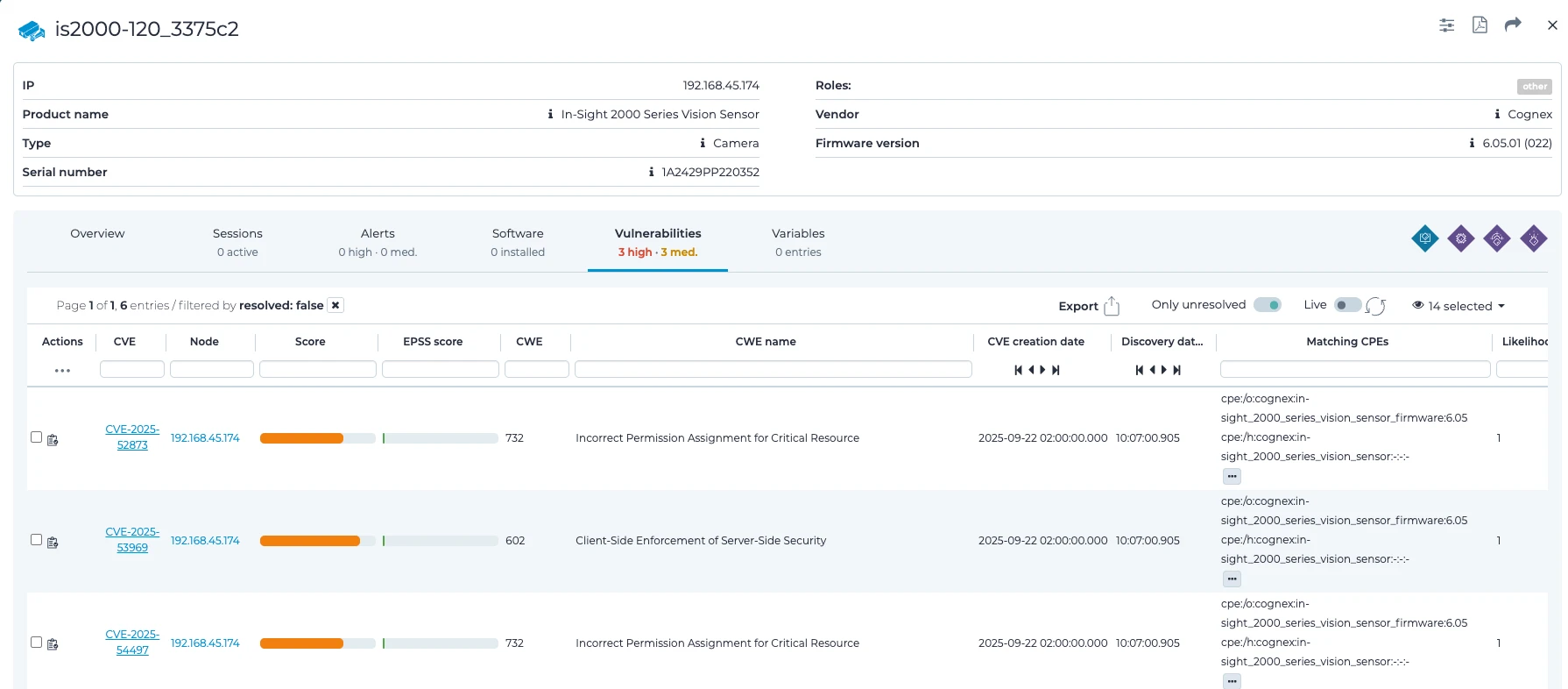
CVE-2025-53969 demonstrates that the authorization controls on the affected devices are insufficient to properly enforce privilege separation, enabling an attacker with valid low-level or restricted credentials to escalate their access to full user privileges.
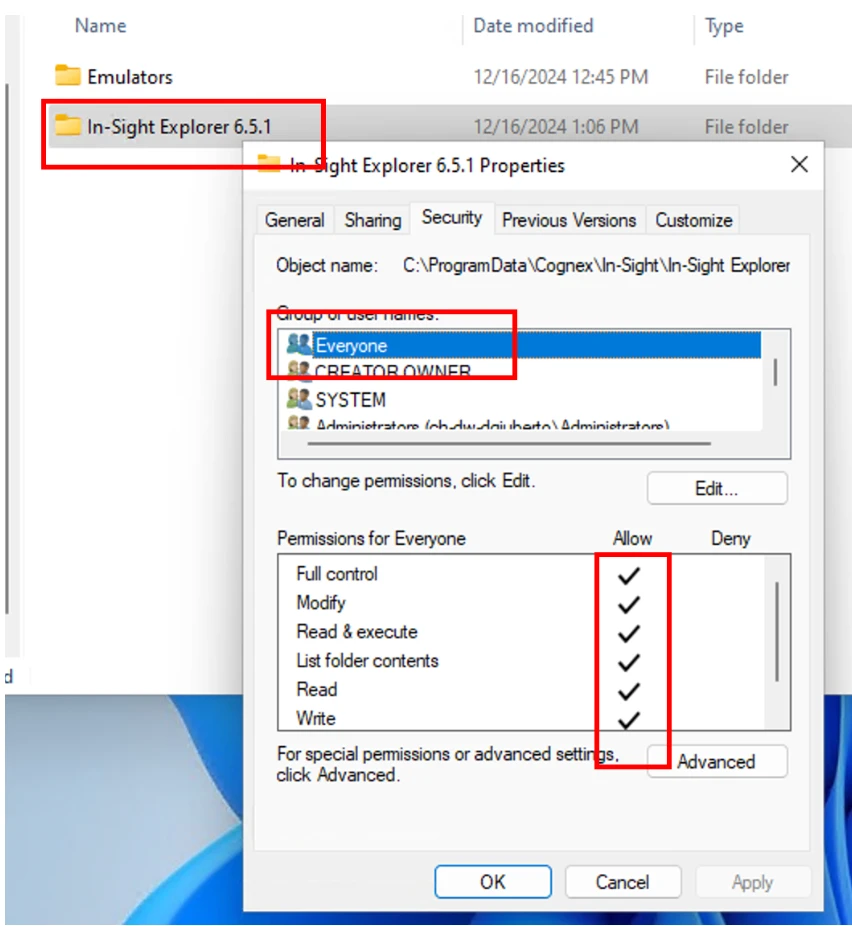
Third scenario: A low-privileged user with access to the engineering workstation running the In-Sight Explorer software, but without direct access to the camera, can still cause disruption by exploiting CVE-2025-53947. This involves tampering with a weakly protected folder at C:\ProgramData\Cognex\In-Sight\In-Sight Explorer 6.5.1 that stores camera backup data. Because backups also contain “jobs” for the camera to execute, modifying these files can cause the device to run malicious or disruptive tasks when restored by an administrator, potentially leading to significant service disruption. Figure 5 shows the list of privileged bound to the C:\ProgramData\Cognex\In-Sight\In-Sight Explorer 6.5.1.
緩和策と提言
Cognex reports that In-Sight Explorer based vision systems are legacy products not intended for new applications. CISA issued a security advisory detailing the flaws, their potential impact, and recommended mitigations. To reduce risk, asset owners are advised to:
- Limit network exposure for all control system devices and ensure they are not directly accessible from the internet.
- Segment control networks by placing them and any remote devices behind firewalls, and isolating them from business or corporate networks.
- When remote access is necessary, use secure methods such as Virtual Private Networks (VPNs). Keep in mind that VPNs may also contain vulnerabilities, so they should be updated to the latest available version. Furthermore, the security of a VPN is only as strong as the devices connected to it.
- Switch to use next generation In-Sight Vision Suite based vision systems, such as In-Sight 2800, In-Sight 3800, In-Sight 8900 series embedded cameras.
To help organizations promptly identify whether the vulnerable device is present in their environment—and to detect and alert on exploitation attempts before they lead to operational disruption, compromise, or further attack progression – customers can rely on the advanced capabilities of Nozomi Networks OT/IoT Security Platform. The platform provides deep visibility into network traffic and device behavior, enabling effective vulnerability and threat detection across OT and IoT networks.
This proactive monitoring empowers security teams to respond swiftly and effectively, minimizing the impact of attacks targeting critical networks. To learn more about Nozomi Networks’ OT/IoT security platform and see it in action, request a demo today.









