北半球では春と夏が最も暑い季節ですが、残念ながらランサムウェア開発者にとっても活発な時期でした。 世界中で、攻撃が成功したとの報告が相次いでいます。その中には、創造性の新たな高みに達したものもあり、例えば最近発見されたAI搭載ランサムウェア(現段階では初期段階のプロトタイプである可能性が高いものの)が挙げられます。これは、侵害リスクを最小限に抑えたい組織にとって何を意味するのでしょうか?本ブログでは、過去6か月間に世界中の実在企業がランサムウェア攻撃に関して経験した実態を共有します。
本稿で言及したデータはすべて、3月1日から8月28日までの期間に、エンドポイントを監視する各種センサーならびに参加顧客の有線・無線通信から収集された、Networks匿名化テレメトリデータに基づいています。
テレメトリが教えてくれること
この期間に最も蔓延していたランサムウェアのファミリーを見てみましょう。 先に進む前に、重要な点を理解しておく必要があります。すべてのアラートが現在進行中の攻撃を示すわけではありません。一部は、ネットワーク構成の変更により当社のセンサーに検知されたものの、被害組織によってまだクリーンアップされていない、かつて活動していたマルウェアのサンプルである可能性があります。さらに、正確なマルウェアファミリーの特定は常に100%正確とは限りません。IPアドレスのような精度が低い侵害の指標(IoC)は、攻撃者によって他の種類の攻撃に再利用される可能性があるためです。
主要なランサムウェアファミリー
5月は当社のセンサーが検知したランサムウェア関連アラートが最も活発な月であり、BlackSuitランサムウェアファミリー が首位を占めました。CISAによれば、BlackSuitはRoyalランサムウェアの直接的な進化形です。両グループを合わせると、身代金として3億7000万ドル以上を受け取っています。 Royalプロジェクト自体は、以前活動していたContiグループの分派と見られており、Nozomi Networks 同グループが活動中だった時期に積極的に追跡・検知を行っていました。
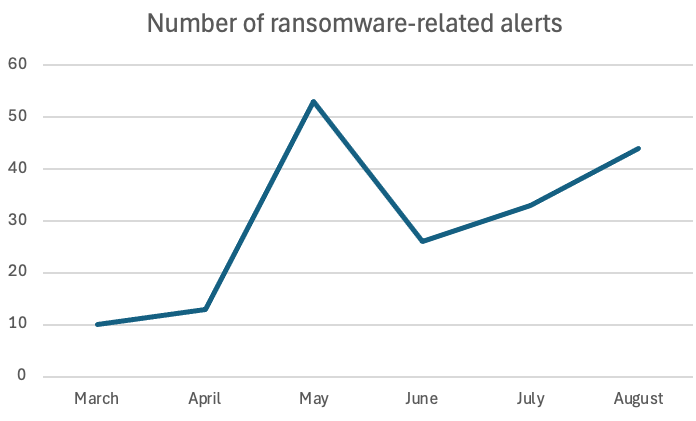
米国政府は7月にブラックスーツランサムウェアファミリーの摘発作戦を実施し、その結果8月にはこの脅威の検知件数が減少した。
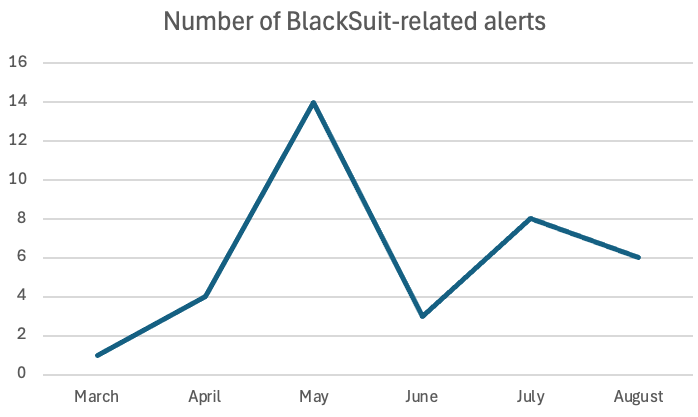
特に留意すべき点は、これらの検知の一部が当社のネットワークトラフィック監視センサーではなく、HMIマシンに配備されたエンドポイントセンサーから得られたものであることです。これらのセンサーにより、異なる視点から潜在的な悪意のある活動を監視することが可能となります。これは、強固なサイバーセキュリティ体制の構築において、多層的なアプローチを採用することの重要性を示しています。
この期間で2番目に活発だったランサムウェアファミリーは、TA505グループによるCl0p/Clopでした。約2年前のマルウェアであるにもかかわらず、企業ネットワークで依然として頻繁に確認されています。これは、マルウェアが一度リリースされると、完全に根絶するには相当な時間を要することを改めて示しています。 2年前、このグループはMOVEit Transfer、Accellion File Transfer Appliance、GoAnywhereソリューションのゼロデイ脆弱性を標的とし、BBC、Boots、British Airwaysなど著名な被害組織を含む複数組織を侵害した。
ブラック・バスタランサムウェアがトップ3の最後を飾る。CISAによれば、昨年半ばまでに500以上の組織が被害に遭った。彼らの活動は今年2月の大規模な情報漏洩で暴露された。これにより組織は活動を控えるようになったものの、既に展開されたランサムウェアモジュールは世界中で検出され続けている。
それでは、最も標的とされている地域を見てみましょう。
主要ターゲット国
過去6か月間にマルウェアに関連する警告が最も多く発生した上位3カ国は次のとおりです:
- アメリカ合衆国 (56.42%)
- 英国(14.53%)
- 日本(6.7%)
米国が首位を占めており、ランサムウェア攻撃者の半数以上がこの国を標的として優先的に狙っています。当社のテレメトリデータによれば、2024年後半においても全体で最も標的とされた国でした。
これらの国々に所在する全ての組織に対し、ランサムウェア攻撃に対処できる態勢が整っていることを確認するため、サイバーセキュリティ対策の見直しを強く推奨します。もちろん、これらの地域外にある組織も、ランサムウェアは国境を越えるため、自社の態勢を再検討すべきです。
最後に、この期間中にランサムウェアによって最も標的とされた業界を見てみましょう。
主な対象産業
主な対象産業は以下の通りでした:
- 製造業(83.82%)
- 運輸(13.87%)
- 消費者向けサービス (1.16%)
製造業界を標的としたランサムウェアの検知件数が全体の83%以上を占める現状は、組織にとって次の攻撃対象となる可能性を警告する警鐘である。包括的な可視性によって戦略的判断を支え、明確かつ強固なサイバーセキュリティ態勢を構築することが極めて重要である。
運輸部門は、検出されたランサムウェアインシデントの13%以上に関連しており、製造業に次いで高い割合を示しています。日常生活の維持に不可欠な運輸システムの重要性を考慮すれば、この事実は過小評価できません。当社の半期ごとのセキュリティレポート最新版では、2025年前半期において最も標的とされる業界でもありました。最後に、消費者サービス組織は全ランサムウェア関連アラートの約1%を占め、このリストを締めくくっています。
概要
コミュニティ全体での積極的な検知技術の著しい進歩やthreat intelligence にもかかわらず、依然として克服すべき課題が複数存在します。組織は、まだ侵害に遭っていないという理由だけで、自社のサイバーセキュリティ態勢が良好であると信じていることが少なくありません。代わりに、堅牢なネットワークおよびエンドポイントの可視化への投資、多層的なサイバーセキュリティ対策の実施、脆弱性管理のベストプラクティスの遵守を通じて侵害の可能性を大幅に低減し、最悪の事態が発生した際には効率的な対応を可能にすることで、関連する損失を防止または最小限に抑えることを推奨します。
Nozomi Networks 、絶えず変化するランサムウェアの動向を常に把握し、 Threat Intelligence マンディアント Threat Intelligence を搭載したTI拡張パックを備えたプラットフォームを通じて、既知および将来のランサムウェアの亜種からお客様を徹底的に保護します。
IoCリスト
- 105.69.155[.]85
- 109.196.164[.]79
- 116.203.186[.]178
- 122.10.82[.]109
- 139.60.161[.]161
- 140.82.48[.]158
- 147.78.47[.]224
- 149.28.200[.]140
- 150.129.218[.]231
- 152.89.247[.]50
- 155.138.246[.]122
- 156.96.62[.]58
- 162.33.177[.]56
- 162.55.38[.]44
- 172.93.184[.]62
- 174.138.62[.]35
- 185.141.63[.]120
- 185.143.223[.]69
- 185.17.40[.]178
- 185.174.101[.]69
- 185.190.24[.]103
- 185.219.220[.]175
- 185.220.100[.]240
- 185.220.101[.]149
- 185.238.0[.]233
- 186.86.212[.]138
- 188.130.137[.]181
- 190.193.180[.]228
- 192.42.116[.]191
- 193.106.31[.]98
- 193.111.153[.]24
- 193.162.143[.]218
- 193.183.98[.]66
- 193.188.22[.]25
- 193.201.9[.]224
- 193.37.69[.]225
- 194.165.16[.]55
- 197.204.247[.]7
- 197.207.181[.]147
- 197.94.67[.]207
- 198.144.121[.]93
- 206.188.196[.]20
- 206.188.197[.]22
- 209.141.36[.]116
- 217.25.93[.]106
- 23.106.122[.]192
- 23.106.223[.]97
- 31.107.255[.]255
- 37.1.212[.]18
- 37.120.193[.]123
- 37.120.238[.]107
- 38.180.81[.]153
- 41.109.11[.]80
- 45.120.53[.]214
- 45.147.228[.]91
- 45.182.189[.]229
- 45.61.136[.]47
- 45.61.138[.]99
- 45.66.248[.]150
- 45.84.0[.]164
- 45.90.59[.]131
- 46.8.16[.]77
- 47.87.229[.]39
- 5.188.86[.]195
- 5.252.23[.]116
- 5.39.222[.]67
- 5.44.42[.]20
- 5.45.65[.]52
- 51.254.25[.]115
- 61.166.221[.]46
- 62.112.11[.]57
- 64.176.219[.]106
- 77.73.133[.]84
- 79.132.135[.]149
- 79.141.160[.]43
- 80.82.67[.]221
- 81.184.181[.]215
- 81.19.135[.]219
- 83.97.73[.]87
- 87.243.113[.]104
- 87.98.175[.]85
- 88.119.175[.]70
- 88.214.27[.]100
- 88.231.221[.]198
- 88.245.168[.]200
- 89.108.65[.]136
- 91.191.209[.]46
- 91.218.114[.]26
- 91.218.114[.]77
- 91.218.114[.]79
- 92.51.2[.]22
- 92.51.2[.]27
- 93.190.139[.]223
- 94.103.91[.]246
- 95.181.173[.]227
- 95.213.145[.]101
- 95.216.196[.]181
- アワーリープロフィットストア[.]com
- provincial-gaiters-gw.aws-use1.cloud-ara.tyk[.]io