With cyberattacks against critical infrastructure constantly changing and evolving over time (https://www.nozominetworks.com/ot-iot-cybersecurity-trends-insights-july-2025), it is more important than ever to focus our efforts not only on detecting known threats but also on building up the capabilities to flag potentially new, previously undiscovered malware. Here at Nozomi Networks, we take this task very seriously, constantly investing our time and effort into both building automation to be able to spot the new threats and promptly reacting to these findings to detect them before significant damage occurs. In this blog post, we talk about how it can be done, what are the obstacles we encounter in this process, and how we address them.
課題
It is easy and straightforward, with the right level of visibility established on the victim’s side, to discover new malware AFTER it was used to successfully perform an attack. All you need to do is to follow classic forensic steps and then connect the dots across various logs and telemetry on the affected system(s). And here we go, now we know that this particular file was part of the process, which means it is malware or a misused dual-use tool. Detecting it at that stage may still be beneficial to the customer if it is done at the earliest stages of the campaign to minimize the damage caused. However, we should aim to detect threats BEFORE the main part of the attack (for example, the Impact tactic) was actually executed and detecting it without access to the forensic data presents a set of big challenges. Let’s talk about them in detail and how they can be handled.
What Level of Visibility Do We Need?
The first problem that many cybersecurity companies face is – how to get access to a narrowed-down list of new malware candidates. The way we solve it is by allowing customers of our Nozomi Networks platform to participate in the telemetry submission process. In this case, apart from using our classic alerting signatures containing already known malicious patterns, we also deploy invisible threat hunting rules. They don’t produce alerts as their logic is very generic, and they can produce a large number of false positive alerts overwhelming SOC analysts. However, some of the samples they detect are new, previously unknown malware.
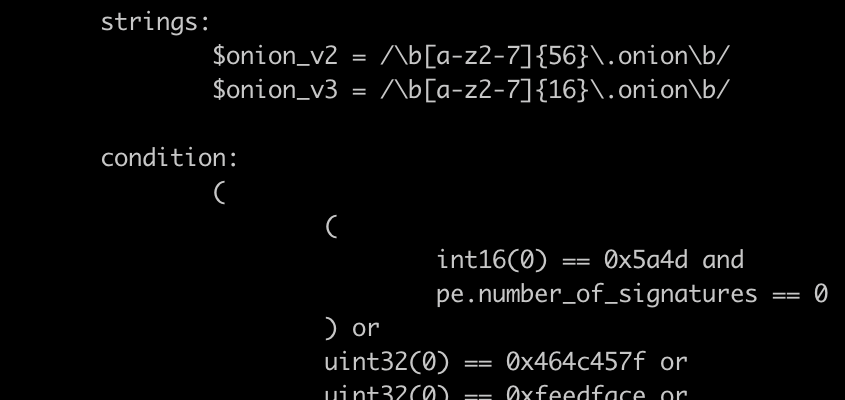
This process is similar to searching for a needle in the haystack. The detected malware candidates are further analyzed by our AI-powered automation to reduce the total volume of them, so that the analysts can focus on analyzing only a small portion of them and remain caught up with this flow of data.
How Do We Correctly Recognize Something That No One Else Has Seen Before?
This may sound like a philosophical question, but when we talk about malware, in many cases it is rather straightforward. First, the crowd wisdom (like detections of other cybersecurity vendors on VirusTotal or information coming from our threat intelligence exchange partners) is very helpful when we talk about threats already known to the public. Secondly, Nozomi developed our own reputation system as well as a scanner that allows us to quickly scan the incoming samples with our own signatures automatically. This way, we can quickly filter out already known/detected samples. Even when analyzing previously unseen samples, many MITRE ATT&CK techniques tend to be implemented in well-established, standardized ways, with relatively little variation.
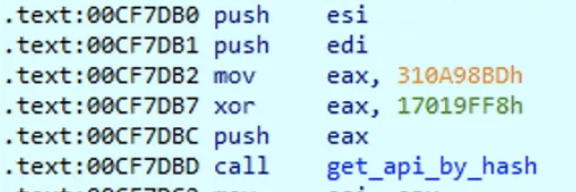
Just recognizing these techniques in the unknown sample performing reverse engineering is enough for an experienced malware analyst to understand whether it is a malware or something benign. In most cases, once malware is first used, the authors continue developing the same project, so the future strains of it still have some features of the previous iterations. Our internal AI-powered classification systems can also assist us in this task by suggesting malware families that this sample can belong to with the corresponding levels of confidence.
Malware or a Custom OT Tool?
As with any activity, there are some corner cases that are hard to handle due to their unique specifics. A great example is the BUSTLEBERM malware that was used against Ukraine last year (https://www.nozominetworks.com/blog/protecting-against-frostygoop-bustleberm-malware).
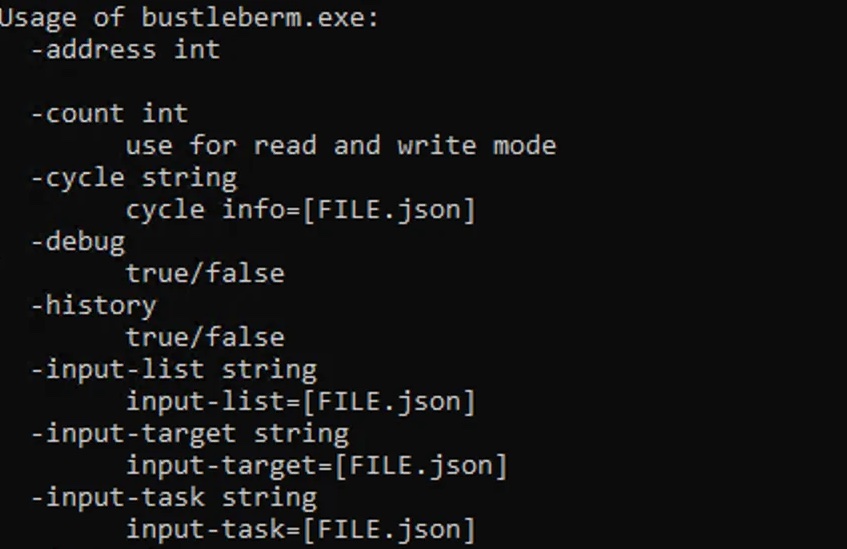
This is a general-purpose tool allowing the operator to change the modbus values. It provides a clean user interface without any major typos or revealing who the authors are or mentioning its actual purpose. Just looking at it without any forensic context, you cannot really tell if it is malicious or benign as it can be used for both purposes, depending on the intent of the user. What should the analysts do when they just encounter this file and it wasn’t used as part of the attack yet? Here are a few things that can help us in the decision-making process:
- Gather as much context as possible from telemetry
Here, our goal is to obtain as much context as possible from the information we collect via telemetry. Knowing from where it was delivered to the victim environment, or what machines it communicates with, or what happened on the same instance/subnetwork around the same time, are all invaluable pieces of information that can help us solve this puzzle. - Detect it regardless of displaying a lower risk score
This is another approach that we follow. In case we don’t know what the sample is, and whether it may be used for malicious purposes or not, we detect it regardless, clearly articulating why we detect it and what the corresponding alert means.
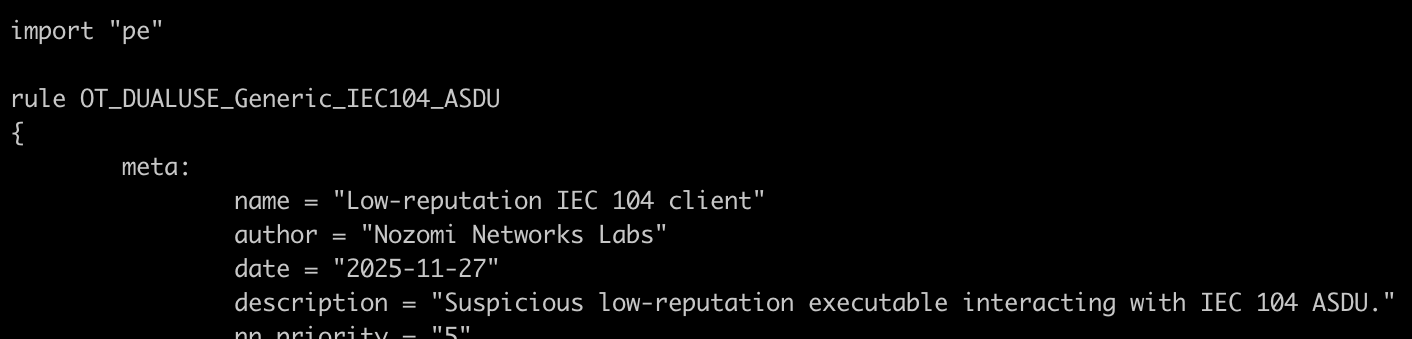
This way, the customer who may have access to more context or have information from forensic activity, can make an informed decision on whether this is a meaningful alert, or it can safely be ignored in their environment where this tool is clearly expected.
概要
Detecting completely new threats is by no means easy, otherwise we would probably never see attacks succeeding. However, it is not an impossible job. Establishing proper visibility in networks and endpoints is the first most important step that all organizations across the globe should have embraced by now. Doing routine vulnerability management is another very important task that organizations should not ignore as it minimizes the attack surface. And finally, by combining various powerful technologies including AI and investing enough resources into this process bear more fruits, allowing cybersecurity providers like Nozomi Networks to further minimize the probability of the potential damage being caused by detecting threats at the earliest stages possible.